During the analysis of a targeted attack, a custom attack utility compiled in 2002 has been found to communicate with servers located in China.
Vtask was written in Visual Basic (VB) and it was designed for lateral movement on a compromised Windows network; its purpose is to hide any active tasks visible on the desktop, thus erasing obvious traces of suspicious activity carried out by the attacker.
Attacker is warned when legitimate users try to log in
Its age is among the most interesting parts of the discovery, since it was created in a time when the technology it relies on had just been introduced in Windows, and analyzing it was difficult because decompilers for VB programs were not available.
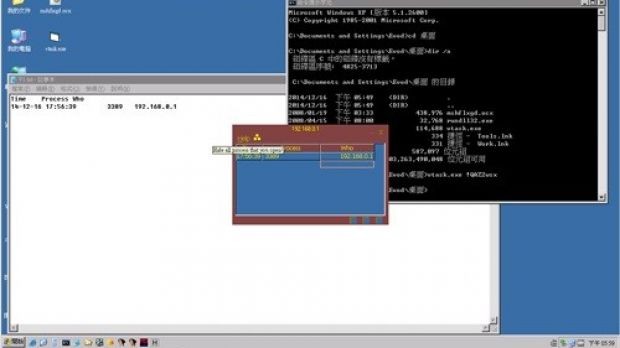
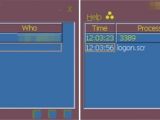
Security researchers from Trend Micro have taken a look at the functions present in Vtask and found that its application window shows the number of users currently logged on the affected system.
A process monitor is also present, offering information pertinent to the attacker, such as the currently running processes; for instance, an active screensaver process reveals that no one is using the computer, giving the attacker the possibility to carry out their operation.
Log-in attempts are signaled to the attacker when the AutoNotice function is enabled by making the main application window flash once.
Immediately after the user logs in, Vtask automatically hides all visible tasks (it does not affect running processes) and the attacker can no longer see the desktop.
The attack tool is more suitable on other platforms than Windows Server because only one user can be logged in at a time. Windows Server editions allow multiple users to be logged in, but they cannot see the desktop of the attacker.
Tool tries to hide IP addresses from China
Connecting to the infected host was carried out through remote desktop sessions, as the technology had just been introduced. Trend Micro believes that software such as Radmin, a remote assistance program, or VNC may have been used by the attacker.
It appears that Vtask is equipped with functions that enable protection of the identity of the operator. “The most interesting part is that Vtask will try to hide IPs coming from a specific IP range, 61.154.x.x, which implies that this is a possible source of attacks. The IP address range traces back to the Fujian region in China,” Trend Micro says.
In order to function, Vtask requires the mshflxgd.ocx library, which is a common one and its presence on the computer does not necessarily indicate a compromise.
The researchers advise organizations to use application control and security and information event management (SIEM) solutions to keep themselves protected against stealthy malicious tools.
On the same note, stripping users of administrator privileges is a good idea, as this measure limits the actions that can be conducted on the network.
 14 DAY TRIAL //
14 DAY TRIAL //