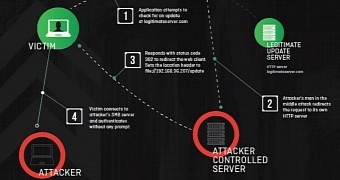
A security vulnerability in Windows operating system that was first documented in 1997 has been adapted to modern times to obtain the credentials of a victim’s machine by causing an authentication attempt to a malicious SMB (server message block) machine.
HTTP requests are used by many Windows applications for different tasks, including checking for new updates. The SMB protocol is for network file sharing and allows clients to connect to a server for read/write operations, as well as for pulling data.
Weak password encryption and MitM attack
The initial vulnerability was discovered by Aaron Spangler in 1997, who found that any URL beginning with “file://” followed by an IP address would cause Internet Explorer 3 to authenticate with the machine at the respective address.
Machines that are improperly configured from a security standpoint will try to log into the SMB server in order to retrieve the resource.
The new variant of the attack, which has been dubbed Redirect to SMB by security researchers at Cylance, consists in intercepting the HTTP requests from applications via the man-in-the-middle (MitM) technique and redirecting them to an untrusted SMB location where the victim’s machine authenticates.
Following this action, the perpetrator collects the password of the target machine, which, although grabbed in encrypted form, could be brute-forced offline because of the antiquated NTLMv2 cryptographic hash algorithm that can be broken with today’s computing power.
According to Cylance, a password of eight characters (upper/lower case letters and numbers) could be guessed in less than 9.5 hours, which would be sufficient for a targeted attack to be successful, considering that companies generally set the lifespan of a password to three months.
Programs from 31 vendors are affected
In a research paper published on Monday, Brian Wallace from Cylance says that the simplest way to exploit the vulnerability is to return an HTTP redirect status code (301 or 302) to inform the client that the resource is available at different locations supplied by the attacker, where authentication is required.
The researcher says that software products from at least 31 companies (the list includes Adobe, Apple, Box, Microsoft, Oracle, and Symantec) are susceptible to Redirect to SMB.
Among the vulnerable products are security products (AVG Antivirus Free, Norton Security Scan, Bitdefender Free Edition, Comodo Antivirus), Microsoft’s IE, Windows Media Player, Excel 2010, productivity tools (Box Sync, TeamViewer) and developer tools (GitHub, PyCharm, IntelliJ IDEA, PHP Storm, JDK 8u31’s installer).
Multiple potential attack vectors, no patch in sight
Apart from the MitM attack that could occur at public WiFi spots, a threat actor could also compromise targets via ARP spoofing, malvertising, browser injection, URL previews for images, documents or websites (some chat applications preview content and the HTTP link could redirect to an SMB location).
Additional attack methods are spoofing or modifying DNS records (DNS cache poisoning), or by sending the victim a maliciously crafted document that initiates an outbound connection (e.g. to check for signature or via embedded scripts).
The flaw affects all versions of Windows, including the unsupported XP and the soon to be released Windows 10.
Microsoft is yet to come up with a patch for Redirect to SMB. In the meantime, the easiest workaround is to block outbound traffic from TCP 139 and TCP 445, Wallace says. On the same note, it is recommended the use of strong passwords that would discourage brute-forcing due to the extensive period required to decrypt it.
Researchers have exploited the vulnerability in AVG Antivirus via ARP poisoning, and in Microsoft Baseline Security Analyzer by changing the DNS records; the videos demonstrating the success are available below.
Targeting AVG Antivirus FREE via ARP poisoning:
Exploiting Microsoft Baseline Security Analyzer by changing DNS records:
 14 DAY TRIAL //
14 DAY TRIAL //