Ten days ago, we reported on a video ads malvertising campaign detected by The Media Trust. According to more information provided by Malwarebytes, that particular campaign that was said to have lasted 12 hours had gone undetected for two months.
After taking a look at the malvertising campaign's data together with ClarityAd experts, Malwarebytes uncovered new clues that show the campaign had first started popping up as early as September.
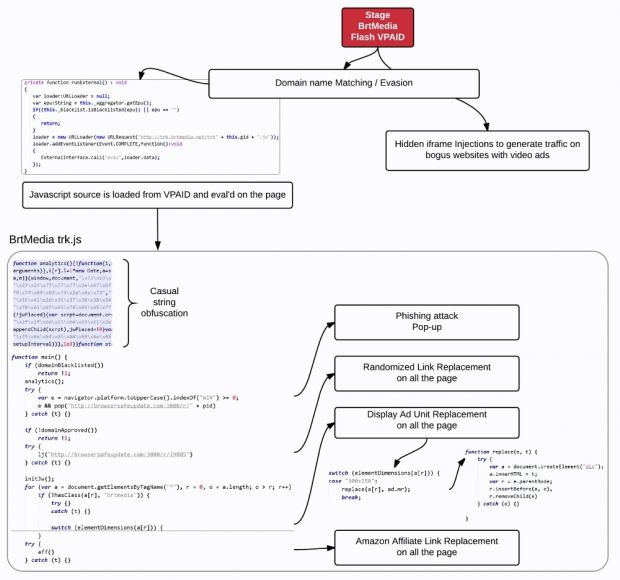
The initial technical analysis was not wrong, and just as previously reported, the campaign used a malicious SWF file hosted on the brtmedia.net domain.
According to Malwarebytes, malvertisers used the LiveRail advertising platform to spread their malicious ads. Whenever the malicious actor won an ad bid, the target website would read ad details from an XML file and download the ad in the form of the infected bidder.swf file.
Researchers blame the VPAID advertising model
Because in recent years online video advertising has moved from the VAST to the VPAID ad format, a much more insecure system, the lack of security limitations in this technology allowed the malicious attacker to pack JavaScript code in the ad's SWF file.
Any video player that downloaded bidder.swf would read the file, find the JavaScript code, and execute directly in the user's browser, instead of a separate iframe.
In the majority of cases, this malicious JS code would try to redirect users to malicious URLs, ask users to update their Flash Player by providing them with a fake update URL, or replace ads on the page with the attacker's own, usually some affiliate links leading to Amazon stores.
In some cases, the malicious code also inserted iframes on the page, where it loaded other websites, trying to boost up their traffic ranking with fake page views.
Malwarebytes didn't say how many sites were affected by this campaign, but the number is obviously much bigger than the first estimate of 3,000 websites.

 14 DAY TRIAL //
14 DAY TRIAL //