Security researchers at Kaspersky have decided to have a look at IoT-enabled devices and their lack of security measures. The results of their experiment, yet again, confirms that Internet of Things devices still lack the proper security measures even today, after years during which many cyber-security vendors have griped about their vulnerabilities.
In their most recent experiment, Kaspersky chose four random IoT devices, which they've meticulously analyzed for any security flaws. The results are a little worrying since all the flaws can be chained together and provide criminals with an attack scenario they can follow and gain access to so-called "smart-homes."
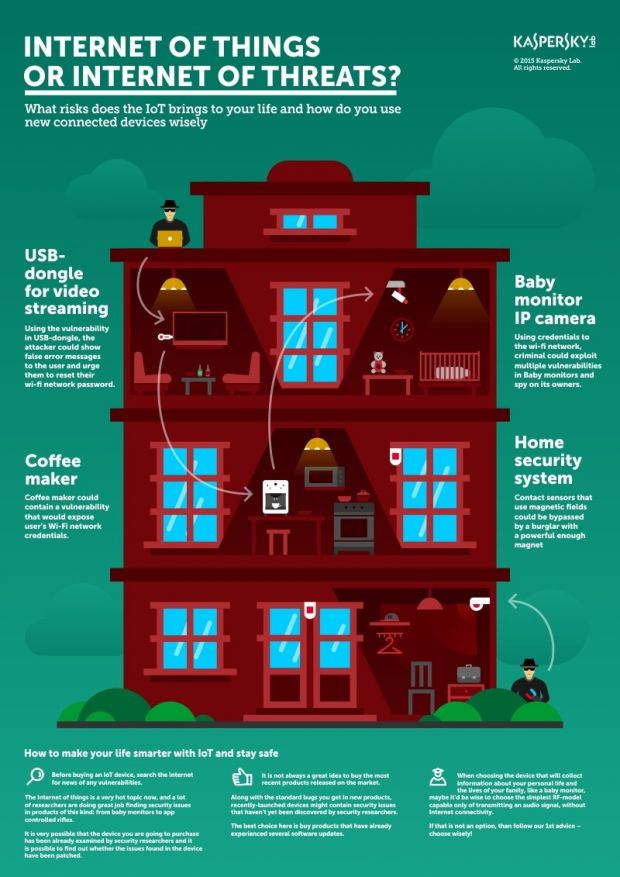
Google Chromecast (USB TV dongle for video streaming)
The first step in such kind of attacks can occur when utilizing the famous "rickrolling" vulnerability in Google Chromecast devices that allows attackers to hijack the content shown on a smart TV.
This can be useful for displaying error messages that fool the user into believing he needs to change his Wi-Fi password or reset the local wireless router to factory default settings, which can easily be leveraged by attackers.
Smart coffee maker (controlled via a smartphone app)
Kaspersky researchers also identified a smart coffee maker device that can expose the user's Wi-Fi password.
Kaspersky declined to name the coffee machine's make and model since the vulnerability has not been patched yet.
As you can imagine, getting hold of a target's Wi-Fi password can grant criminals access to a person's entire portfolio of IoT devices, since all work and use the home's Wi-Fi network.
IP camera (used in webcams and baby monitors)
In Kaspersky's scenario, by leveraging the access the coffee maker gave the attackers by exposing the Wi-Fi password, they can then spy on the home's owners and see when they leave their house.
Criminals can do this by connecting to local IP cameras, if present, but also to baby monitor devices.
We already covered the security issues baby monitors expose their owners to in a previous, more detailed story.
Home security systems
Once criminals know the house owner is not at home, they can leverage a fourth security issue discovered by Kaspersky's staff in an unnamed home security system.
While the researchers were happy to find that the home security system was very well protected against software attacks, the same could not be said on the hardware side.
Apparently, there's a way to trick both contact and motion sensors employed by the system. Researchers found out that by using a very powerful magnet, attackers could open doors and windows without triggering the alarm.
Additionally, since the motion detection sensors worked only with "warm" objects, putting on some clothes that hid the criminal's body heat was enough to make the sensors stay quiet.
All it takes now is a bunch of determined criminals that know what to look for.

 14 DAY TRIAL //
14 DAY TRIAL //