With the release of OS X El Capitan, Apple has bundled with their operating system a new security feature named System Integrity Protection (also known as SIP and Rootless) and designed to block access to a number of system locations, as well as to restrict access to system processes as a measure against the core of OS X being tampered with.
The System Integrity Protection feature does not allow the /bin, /sbin, /usr and /System folders on your Mac to be modified, with the /usr/local, /Applications, /Library and ~/Library folders being accessible by developers.
Moreover, no application can perform any runtime attachment and code injection tasks because these types of tasks can only be performed by the Apple Installer and the Software Update utility from Apple-provided packages.
Furthermore, if you have been using custom kernel extensions, you will no longer be able to do so unless they are signed using a Developer ID for Signing Kexts certificate. Also, from now on, the kext-dev-mode is obsolete, and you will no longer be able to use unsigned kernel extensions as long as SIP is enabled on your Mac.
According to Apple, SIP blocks access to protected system resources even if the user tries to access them using administrative privileges. This means that even if you can log in as the root user (the one that gives you full access to all rights and permissions on a UNIX system), you will not be able to override OS X's System Integrity Protection.
Also, this translates into none of the OS X apps that need access to system resources blocked by the System Integrity Protection feature being able to run properly.
Fortunately, if you install all of your apps from Apple's Mac App Store, you will not have any problems because Apple's sandboxing policy already prevents them from accessing the resources SIP blocks.
However, System Integrity Protection might create serious problems if you use applications distributed by their developers outside of Apple's Mac App Store ecosystem, because their system resources (folders to write to, system processes to attach to or system processes they need to inject with code) are in direct conflict with what OS X's SIP feature considers to be off-limits.
Even though this means that it is also a lot harder if not completely impossible for malware to infect your Mac, it also means that you will not be able to use some of your favorite applications that need access to some of the resources blocked by the Rootless feature.
For example, TotalFinder, Default Folder X, TotalTerminal, and TotalSpaces are some of the apps I cannot use without disabling SIP, and I am still thinking if it is really worth it to disable it for an added amount of help in streamlining my workflow.
Now, you also have to choose between security and convenience, and if you really cannot live without some OS X app that will no longer run on OS X El Capitan because System Integrity Protection is enabled, it is quite simple to disable it completely.
Although disabling the Rootless might put your Mac at risk, you can minimize the chances of malicious software affecting your computer if you follow my tutorial on how to use a Mac and still feel safe even though you do not have an anti-malware solution installed.
| To turn off OS X's System Integrity Protection security feature, you can follow the steps detailed below: |
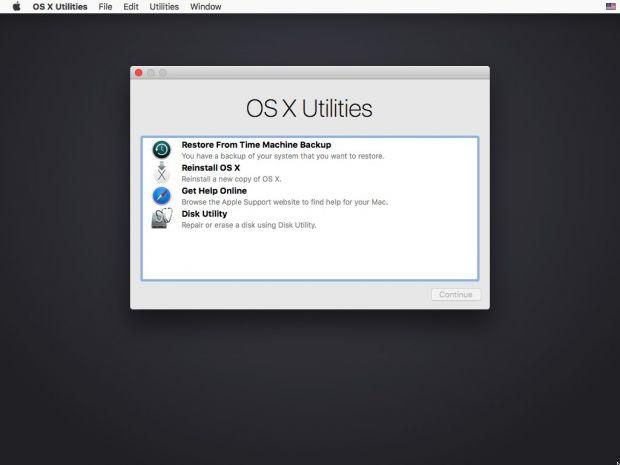
Step 1 - Boot to Recovery OS
First of all, to disable System Integrity Protection you need to boot into the Recovery OS. To do that, restart the Mac by going to the menu and clicking on the Restart option.
Next, immediately hold down the ⌘ + R keys on your keyboard and release them once the Apple logo is displayed on the screen.
Once the Recovery OS loads, go to "Utilities" in the menu and click on the Terminal entry.
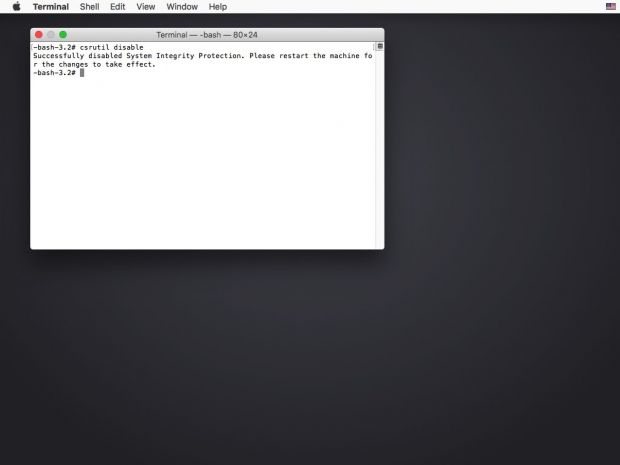
Step 2 - Disable System Integrity Protection
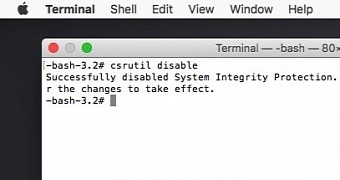
After the Terminal opens, type in the following command:
If you change your mind and decide that using an extra app or two is just not worth it, and the security risk is too high, you can turn on System Integrity Protection back again by booting into the Recovery OS once more as described in the first step, opening the Terminal, and entering the following command:
Step 3 - Restart your Mac
To apply the changes you've made to the System Integrity Protection feature, you have to restart your Mac by going to the menu and clicking on the Restart option.
Why you shouldn't disable Rootless on your Mac
Disabling the OS X System Integrity Protection feature or not is a matter of choice, but if you choose to do it, you now know exactly how it should be done.
However, you should keep in mind that OS X's SIP feature has been integrated by Apple as an extra measure against malicious software wreaking havoc once it manages to get access to the system's root user.
Having Rootless enabled is a very simple way of preventing malware from modifying any OS X resources it needs to multiply and spreading itself throughout the system, and one of the extra measures you should take if you're against installing an anti-malware solution on your Mac.
With this word of advice in mind, leave a comment below if you have further questions regarding the SIP disabling process described above or if you want to share your thoughts on this subject with the rest of the readers.
 14 DAY TRIAL //
14 DAY TRIAL //