The Ubuntu Touch platform is still very young, and it doesn't have millions of apps in the store, but someone has just uploaded a malicious one that managed to get past the automated testing.
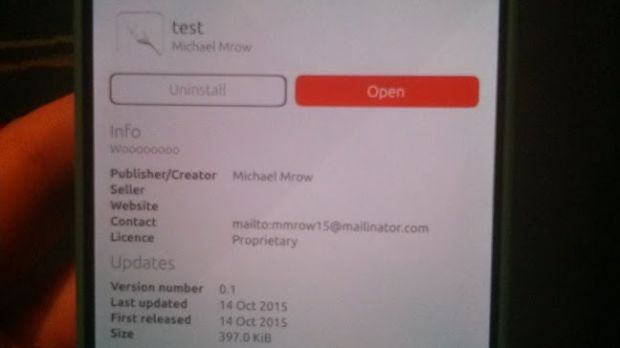
One of our readers sent us a notice about a new application that's been uploaded to the store, which was simply named "test" (removed in the meantime) and was able to change the boot splash for the phone.
This is not something allowed, and it's not clear if the application did anything else. The advice from the Ubuntu developers is to uninstall the application. An application capable of doing that (and possibly more) is a dangerous thing to have around, and Ubuntu developers have been quick to remove it.
At this point, it's not exactly clear how many people downloaded it, but it was reported pretty fast by the community, so it's unlikely that too many people got it. Also, it has a generic name, so it's not like it popped up in searches. A much more important problem is the fact that it passed through the regular security filters, and that such important modifications were possible.
Canonical responded immediately
The Ubuntu developers will have to reassess the security measures they have in place for Ubuntu Touch, and they need to make sure that the problems will be quickly fixed. Since this is the first malicious app that made it into the store, it's a pretty big deal.
"It has come to our attention via our community that a potentially malicious application has been submitted to the Ubuntu Store. We have identified that you are one of the users who downloaded the application. We have removed the application from the store as soon as we were made aware and are taking steps to ensure this does not happen again. The application is called 'test' published by developer mmrow, version 0.1 and only affects armhf based mobile devices," reads the email sent by Canonical.
Users have been advised to uninstall it as soon as possible, so hopefully whatever the problem was, it will soon be fixed. We'll probably see something in the changelog for the next OTA update in this regard. We also have a video via one of the Ubuntu community members (many thanks to Szymon Waliczek for taking the time to do this).
Update: Here is the first update from the Ubuntu Community Team Manager, David Planella:
"Thanks to the quick reaction of our community, Canonical was equally reactive and able to put together a task force to investigate and take immediate measures to identify and resolve issue.
As pointed out in the article, the handful of users affected were contacted directly after an understanding of the incident had been gathered, and additional measures were taken so that no other users could be affected by the exploit.
After the initial analysis, no other apps or users are affected, the main issue has been identified and a fix deployed. The Ubuntu Store is functioning normally and apps can be securely installed as usual. We are continuing with the security analysis of our tools and infrastructure to ensure there are no further implications and will publish the full details shortly."
 14 DAY TRIAL //
14 DAY TRIAL //