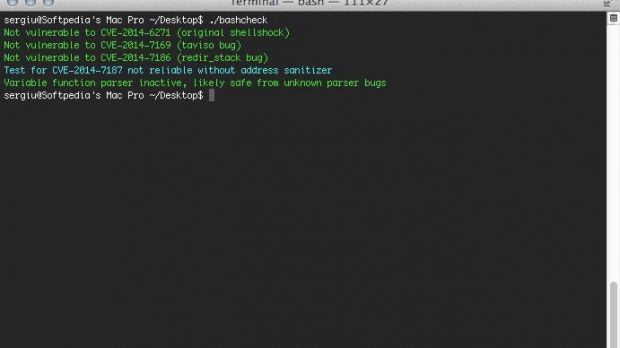
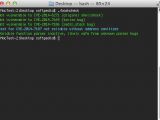
A Shellshock vulnerability checking tool called “bashcheck” has been used to test the latest patch from Apple against the 22-year-old glitch, and showed OS X to be vulnerable to the issue discovered by Florian Weimer and identified as CVE-2014-7186.
A security update for OS X was released on Monday by Apple, aimed at Lion (10.7), Mountain Lion (10.8) and Mavericks (10.9) systems and set to address the Shellshock bug in the Bash command-line tool.
Dev eliminates false positive
Bashcheck is designed to verify the command-line tool in OS X against all the security flaws related to the Shellshock bug; as it happens, the script had a flaw of its own and showed that the shell was vulnerable to an out-of-bound memory read error in redir_stack (Weimer’s glitch).
This was repaired by its developer, Hanno Böck, who made the tool available on GitHub. Böck also disclosed that a new line has been added, to “fix redir_stack false positive;” but it appears that plenty of users had already used Bashcheck and saw that the fix from Apple failed to protect their systems against the threat.
Open-source community finds fix, then Apple releases update
After the initial discovery of Shellshock (CVE-2014-6271), a security flaw that has been available in Bash for more than 20 years, developers were quick to release a fix. However, the patch was incomplete and a new glitch (CVE-2014-7169) popped up.
Another update for Bash followed, and two new problems were detected (CVE-2014-7186 and CVE-2014-7187), so the code for the shell was modified once more. Florian Weimer, product security researcher for Red Hat, also provided a patch for both of them.
The list of issues resulting from the original Shellshock did not stop there though, as Google security researcher Michal Zalewski found two more vulnerabilities (CVE-2014-6277 and CVE-2014-6278), one of them being as dangerous and easy to exploit as the initial bug.
In the security-announce mailing list, Apple clearly states that their fix is designed for the first two problems in Bash (CVE-2014-6271 and CVE-2014-7169), but they also included some changes that “added a new namespace for exported functions by creating a function decorator to prevent unintended header passthrough to Bash.”
Apple explains that after applying their variant of the patch, environment variables introducing function definitions require “a prefix ‘__BASH_FUNC<’ and suffix ‘>()’ to prevent unintended function passing via HTTP headers.”
Weimer’s patch, which is at the moment the latest and greatest against the Bash bug, also uses prefixes and suffixes for separating the namespaces for shell functions.
[UPDATE 10.02.2014]: Hanno Böck, the developer of Bashchecker contacted us to say that the fix mentioned in the article was not related to OS X and that the CVE-2014-7186 vulnerability on Apple’s operating system was present at the time of our testing, and still exists.
The false negative we received in our assessment of Bash on OS X was due to the fact that the script was undergoing modifications and not everything had been fixed.
Böck told us that “the first fix was wrong and it created some false negatives on other systems.
It was a bit tricky to get it in a way that it works everywhere and I did various commits. I think you ran one of the intermediate versions with false negative reports about CVE-2014-7186.”
After running a new test with the final version of Bashchecker, the script reported that the system was vulnerable to CVE-2014-7186. However, the glitch cannot be exploited thanks to Apple adding prefixing requirements in the patch.
This basically means that OS X users are not in danger of falling victims to attacks leveraging the aforementioned Shellshock security issue.
 14 DAY TRIAL //
14 DAY TRIAL //