Users are unnecessarily putting themselves at risk by downloading apps from third-party stores, some of which are contaminated with ANDROIDOS_LIBSKIN.A, one of the most recent malware families spread through these types of unofficial app portals.
The dangers of installing Android apps from outside the Google Play Store are as well documented as the risks of installing iOS apps from outside the Apple App Store are. Users have been warned against this practice for years, but third-party app stores continue to exist and thrive.
Alerted by data received via the company's Mobile App Reputation Service, Trend Micro came across a new malware family targeting Android devices, currently spread only via third-party stores.
ANDROIDOS_LIBSKIN.A can root your Android phone
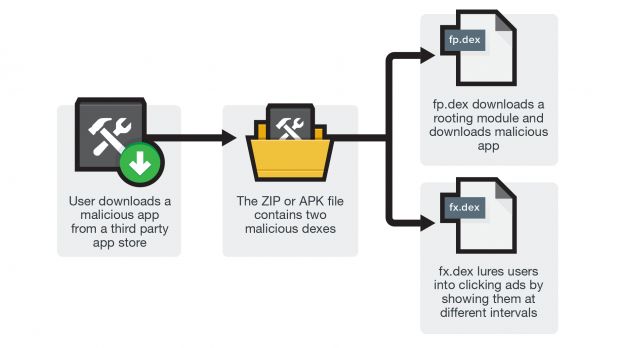
This new threat, named ANDROIDOS_LIBSKIN.A, has a relatively simple infection chain. The malware is bundled with copies of legitimate applications, which some users end up downloading on their devices.
Once the app is downloaded and installed, it loads the libskin.so shared library, which contains an exploit that roots the device and gives the malicious app absolute power over your device.
From here on out, the ANDROIDOS_LIBSKIN.A malware uses two other files, fp.dex and fx.dex, which download and install other apps and also show unwanted ads.
On top of this behavior, researchers also saw this app collecting information on all infected users, and sending it to a remote server where the attackers are building a database of infected devices.
The malware includes functions that allow it to collect data such as subscription IDs, device ID, language, network type, a list of active apps, network name, and many other more.
Third-party stores were notified but never took down the apps
Trend Micro says it spotted these malicious apps in third-party stores like Aptoide, Mobogenie, mobile9, and 9apps. The company informed each one, but they claim none responded to their emails.
Additionally, unlike other vendors that just release "threat alerts" about malicious apps but never release their names, Trend Micro has also compiled a list that contains both the app's name and its SHA1 hash.
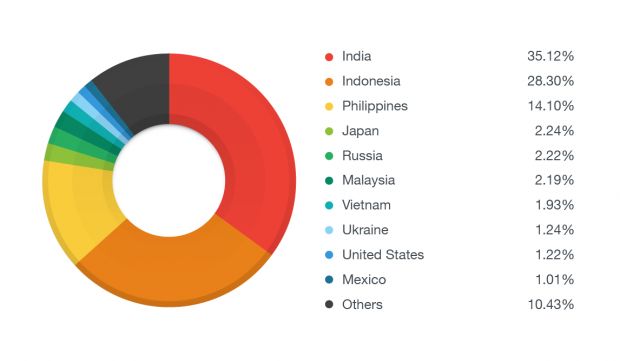
At the moment, the most users with infected ANDROIDOS_LIBSKIN.A devices can be found in India, Indonesia, and the Philippines.
 14 DAY TRIAL //
14 DAY TRIAL //