Security researchers from Kaspersky have revealed interesting insights about the Adwind RAT (Remote Access Trojan), its numerous clones, and its mode of operation.
An RAT is a piece of malware that infects a user's computer and secretly steals their data while also allowing a hacker in a remote location to access the device and even control it if they want to.
There are lots of RATs on the underground malware market, and one of the biggest and most known is the Adwind RAT, which Kaspersky's team has unraveled at this year's Security Analyst Summit (SAS 2016) held in Tenerife, Spain.
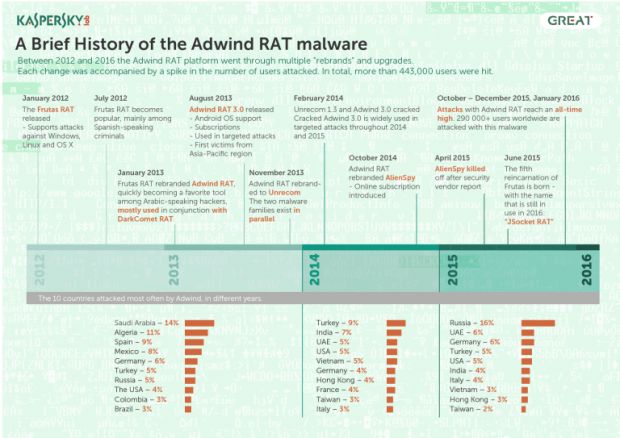
Adwind has gone through five different iterations
First appearing on the market in January 2012 under the Frutas RAT name, the RAT's control panel only featured a Spanish interface and was marketed to only a handful of countries.
As the developer managed to rack up funds from his initial effort, he rebranded the tool under the Adwind RAT name in January 2013, added an English interface, and also support for Android devices, on top of the initial support for Windows, Mac, and Linux.
With Adwind becoming more and more successful and drawing the attention of more law enforcement agencies, the developer rebranded it in February 2014 (Unrecom RAT) and then in October 2014 (AlienSpy), before settling on its current name in June 2015 (JSocket RAT).
Names changed, capabilities evolved
Very few malware families manage to survive more than a few weeks, let alone four years. Adwind's success can be attributed to a series of factors.
Frist of all, the RAT was a success because it was written in Java, allowing it to function on four different operating systems (Windows, Mac, Linux, Android). Even if it relied on users having the Java environment installed locally and victims double-clicking Adwind's .jar file, the developer got crafty, and on platforms where Java wasn't installed, it would bundle the Java installer with the RAT, and set up both at once.
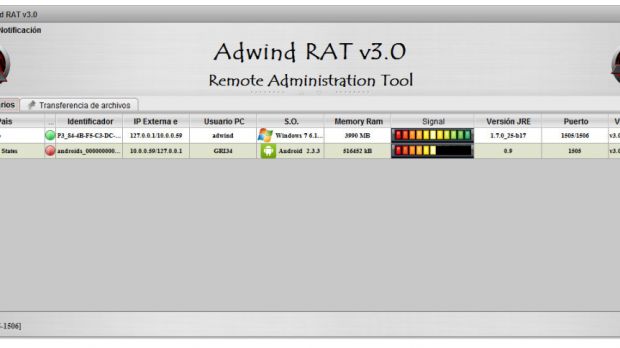
Secondly, Adwind's creator never stood idle, and as time went by, he continued to add more and more features to the RAT's arsenal. As it is today, Adwind is one of the most dangerous spying tools around, allowing intruders to: ► log keystrokes ► steal passwords ► get data from Web forms ► take desktop screengrabs ► take webcam screenshots ► record webcam video ► record microphone sound ► steal files ► steal cryptocurrency wallet keys ► steal VPN certificates ► collect general system info on each infected device ► manage SMS messages on Android
Adwind ran as an RAT-as-a-Service
These diverse features made sure the RAT was a success, and in the end, it was no surprise that the malware's creator decided to shift from a pay-per-instance commercial model to a hosted, subscription-based service, which allowed him to charge monthly for access to his tool. Prices went from $30 (€27) to $200 (€180), based on the capabilities you needed.
Using rough calculations, Kaspersky estimated that the Adwind author made around $200,000 (€180,000) per year, sold the RAT to around 1,800 people, who then used it against 443,000 victims.
In most cases, Kaspersky says that the individuals that bought Adwind used it for targeted attacks, meaning against one or very few individuals, not for mass surveillance.
This limitation was due to Adwind's mode of operation, which collects vast amounts of data and can sometimes overwhelm C&C servers when used on multiple targets at once.
Since Adwind's author has showed that he doesn't mind scratching an Adwind business and starting over again under another name, Kaspersky and law enforcement officials have a hard time shutting down the operation, which is still online as we speak.
If you're in the mood for an 83-page report, you can learn more about Adwind from Kaspersky's investigation.
 14 DAY TRIAL //
14 DAY TRIAL //