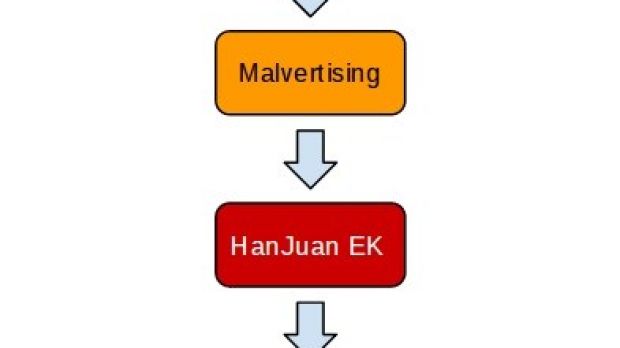
Security researchers identified a new malvertising campaign leveraging advertising service Ad.fly to redirect users to HanJuan exploit kit and ultimately compromise systems with malware designed to steal login credentials.
HanJuan is rarely encountered in security incidents, which kept it under the radar. There isn’t too much information about it, but in the past it was seen to deliver an exploit for a Flash Player zero-day.
Ad.fly is a URL shortening service that shows an advertisement before the user can access the content available at the short link.
Exploits for Flash and Internet Explorer delivered
Jerome Segura from Malwarebytes has analyzed the current campaign and noticed that it relies on a complex redirection chain until users are passed to a legitimate location that has been compromised to host the exploit kit.
To thwart analysis, cybercriminals resorted to cross-origin resource sharing, a mechanism that allows resources to be loaded on a web page from a different domain than the one for the parent web page, creating a disruption in the resource loading flow.
Segura says that the landing page for HanJuan contains code for launching exploits for a Flash vulnerability (CVE-2015-0359) and one in Internet Explorer (CVE-2014-1776), depending on the profile of the visitor.
Final payload does not appear to target banking info
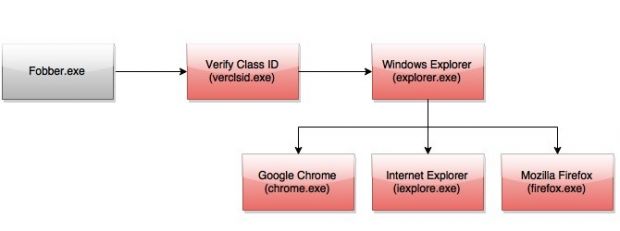
The payload is a malware that injects any of the three major web browsers (Internet Explorer, Chrome and Firefox) and monitors web activity waiting for login pages for targeted online services.
The threat has been dubbed Fobber by Malwarebytes, but Dutch security company Fox-IT has identified it as a new variant of Tinba (Tiny Banker) banking Trojan.
“To do this, it compares the URL in the request to list regular expression strings that are decoded in memory,” Segura says in a blog post published on Wednesday.
Upon finding a login request matching the expression, Fobber harvests the username and password (data is encrypted using a custom algorithm) before they are encrypted by the browser and sends the info to a command and control (C&C) server.
HanJuan has gained the reputation of a stealthy exploit kit, which makes its involvement in a malvertising campaign a rather irregular move, Segura says, because it places it in the spotlight of security research.
 14 DAY TRIAL //
14 DAY TRIAL //