A vulnerability exists in the way Xiaomi’s Mi Market app connects to retrieve applications from the eponymous Android store curated by the company, potentially impacting millions of users.
Since Google services are not available on the Chinese market, Mi Market fills the gap, delivering content via the app developed by Xiaomi.
Mi Market is not exclusive to Xiaomi phone users and can be downloaded separately to get apps and games in Chinese. Android phones from the company sold outside China come pre-installed with Google Play.
Malicious apps can be pushed to users
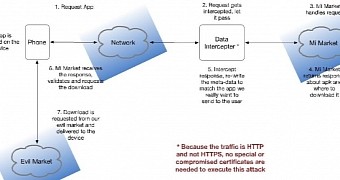
Bluebox mobile security company found that a recent version of the store app did not rely on a secure connection neither for connections or content delivery and the exchange was carried out via the plain HTTP protocol.
The risk associated with this practice is well known, as threat actors can easily intercept the traffic and modify it by sitting between the client and the Mi Market server, in what is called a man-in-the-middle (MitM) attack. This can be pulled by gaining control of a Wi-Fi hotspot.
Using this technique, cybercriminals can replace apps requested by users with malicious variants impersonating the original that can steal sensitive information like login data for online accounts or banking credentials.
Marketplace permissions allow the fake app to install silently on a Xiaomi device, while on other phones user confirmation is required for the action to complete. However, this does not increase security if the evil version looks like the real one.
Patch does not eliminate the problem for all users
The Chinese manufacturer released a fix on April 27, to all its users, in MIUI ROM 6.5 (Xiaomi’s custom Android-based operating system), but phones relying on a different system version and those running Mi Market (e.g. R.1.4.4) as a third-party app on non-Xiaomi devices are still vulnerable.
Andrew Blaich, lead security analyst at Bluebox, says that new tests carried out after applying the update found that a secure protocol (HTTPS) was enforced for the main app requests.
However, HTTP is still used for other metadata requests and for downloading the app, the researcher adds. This means that the APKs (Android app installation file) could still be susceptible to being replaced in transit.
Blaich also draws attention to the fact that Mi Market does not use certificate pinning, a mechanism that would foil an MitM attack by validating certificate info advertised by the server with the original data included in the app.
"This means that the Mi Market is still susceptible to man-in-the-middle (MITM) attacks through methods such as a compromised or maliciously controlled certificate authority," Blaich explains.
This type of attack is more advanced and costing, although motivated threat actors could resort to it.
Xiaomi sold about 61 million devices in 2014, and this year the goal is to pass the 100 million mark.
 14 DAY TRIAL //
14 DAY TRIAL //