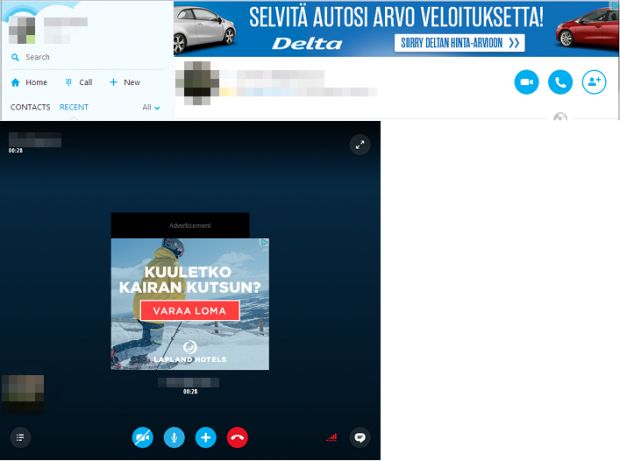
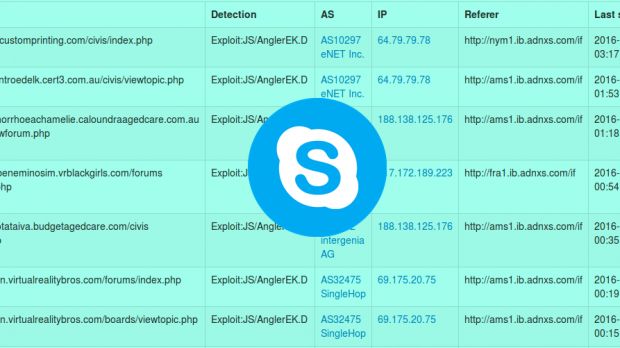
Security researchers from F-Secure have uncovered a brief malvertising campaign that has hit Skype users, in what seems to have been an accidental infection.
Malvertising is the operation of delivering advertising laced with malicious JavaScript code that hijacks the user's browsing experience and takes them to a rogue Web page, where attackers employ automated software called exploit kits to scan the system for vulnerabilities and abuse them to infect the user's PC with malware.
Theoretically, malvertising works in all mediums where ads can be shown. In practice, malvertising is only effective in browsers, since exploit kits are often configured to exploit browser-specific issues.
In the most recent case of a malvertising campaign, researchers from F-Secure observed a spike in malicious ads delivered to Skype users.
While harmless when shown inside Skype, F-Secure researchers investigated this campaign further and discovered it was also delivering malverts (malicious ads) to browsers.
The malicious ads were being shown on sites like eBay.it and were leading users to the Angler exploit kit, which was delivering the TeslaCrypt crypto-ransomware.
Criminals used the AppNexus ad platform (adnxs.com) to display the malicious ads, but researchers said the campaign was short-lived probably because the criminals noticed their blunder and shut it down to reconfigure their attack.
This is not the first time when malicious ads were delivered to Skype, as something similar happened in 2014 and 2015.
 14 DAY TRIAL //
14 DAY TRIAL //