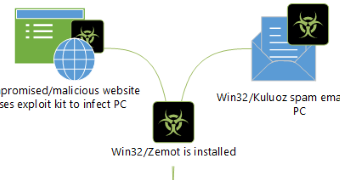
Zemot dropper is a strain of the Upatre malware dowloader that has been observed by security researchers to benefit from multi-distribution points that include both compromised websites as well as the Asprox/Kuluoz spam botnet.
Microsoft noticed activity from TrojanDownloader:Win32/Upatre.B back in late 2013 and determined that it is preferred by cybercriminals for the distribution of a two pieces of click-fraud malware (PWS:Win32/Zbot.gen!AP and PWS:Win32/Zbot.CF).
In May 2014, the company decided to rename Upatre.B to Zemot in order to differentiate between the two threats that are similar in nature but with certain particularities that set them apart, enough to label them as a new malware family.
Zemot is part of a network with a complex structure that involves various types of malware. Researchers say that the dropper is delivered to the victim’s computer through exploit kits Magnitude and Nuclear Pack, or it can be distributed via Kuluoz spam-sending botnet.
Once Zemot is on the system, it starts funnelling in click-fraud malware. However, Microsoft says that recently, other types of threats have also been distributed (Rovnix, Viknok and Tesch), which can be employed for downloading new malware or for stealing sensitive information.
It is a complex infection chain that can rely on several droppers until the payload for the info-stealing malware reaches the infected computer.
In its analysis, Microsoft notes that Zemot appeals to several techniques to ensure that the downloaded module will be successful on all Windows platforms.
It also stores all downloaded files under unique file names that not only contribute to evading detection but to the increasing the number of infections of the same machine, too.
Furthermore, Microsoft says that “modules such as getting the OS version, user privilege, URL parsing and the downloading routine are taken from the Zbot source code.”
Another particularity for the Zemot family is that multiple variants can be distributed with other malware, since one dropper can spread multiple malicious payloads.
Telemetry data from the company shows that this strain has been on a downward spiral since June and in August the number of machines infected was up to 30,000.
The same was recorded from information regarding file count, a spike in activity being registered in June (almost 20,000), followed by a decrease to less than 10,000 files in August 2014.
In a blog post published on September 9, Microsoft announced that the routines for removing Zemot family tool from an affected system have already been integrated into the Malicious Software Removal Tool.
 14 DAY TRIAL //
14 DAY TRIAL //