Dubbed Xsser mRAT (mobile remote access Trojan), the newly discovered remote access Trojan for the iOS platform was found by researchers to be hosted on a server used to deliver Android spyware to protesters in Hong Kong.
Security experts do not know how an attack with Xsser would be carried out, but by analyzing the threat, they discovered that it was an advanced remote access Trojan devised specifically for jailbroken iOS devices.
Xsser mRAT for iOS steals plenty of information
Lacoon Mobile Security encountered the threat while investigating Android spyware distribution among the Hong Kong protesters. The threat came as an app purporting to be designed for coordinating the manifestation, via a link in an anonymous Whatsapp message.
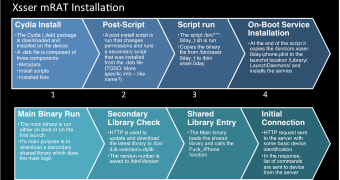
After investigating the origin of the malware, the researchers found that the command and control (C&C) server stored a Cydia repository for an iOS Trojan; Cydia enables installation of software packages on jailbroken iOS devices.
Closer examination showed that the malware could exfiltrate various sensitive information from the affected phone.
The contact list, text messages, call logs, OS data, location information based on cell ID, as well as passwords can all be stolen by the operators of the threat. Other authentication data, such as keychains used by AppleID, email and other apps from Apple, is also targeted.
According to Lacoon, Xsser mRAT can run immediately after boot and can be updated dynamically, downloading the latest resources as needed.
The initial information delivered to the C&C servers includes the version of the operating system, MAC address, device version, IMSI and IMEI codes, and the phone number of the victim.
Only after these details are sent does the malware receive the commands for stealing the aforementioned data from the server.
Chinese government suspected
In a company blog post, Ohad Bobrov, co-founder and CTO of Lacoon, said that the cyber-activity could have been initiated by the Chinese government.
“Cross-Platform attacks that target both iOS and Android devices are rare, and indicate that this may be conducted by a very large organization or nation state. The fact that this attack is being used against protesters and is being executed by Chinese-speaking attackers suggests it’s first iOS trojan linked to Chinese government cyber activity,” he writes.
The features of the malware also seem to come in support of this theory, as it is the first fully operational Chinese Trojan for iOS uncovered to date.
It may be leveraged against the protesters, but its use could go far beyond this. Bobrov notes that it could be employed in cyber-espionage operations to spy on companies or key targets.
 14 DAY TRIAL //
14 DAY TRIAL //