A warning has been issued by security researchers about malicious actors being able to remotely install and launch arbitrary apps in Play Store by exploiting a cross-site scripting (XSS) or a universal cross-site scripting (UXSS) vulnerability in Google’s web app for the marketplace.
In a UXSS attack, client-side vulnerabilities are exploited in a web browser or a web application and generates an XSS condition, which can allow execution of code, bypassing the protection mechanisms in the browser.
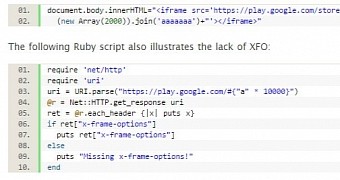
Flaw demonstrated with JavaScript and Ruby code
The flaw results from the fact that the Play store app does not include complete coverage for X-Frame-Options (XFO) support, which are an HTTP response header that indicates if a web browser should be permitted to load a page in a frame.
Malicious actors often rely on this technique to trick users into believing that content in an iframe comes from a trusted source.
The potential risk is for users of JellyBean (4.3) and earlier versions of Android, which no longer receive official security updates from Android security team for WebView, a core component that renders web pages.
Tod Beardsley from Rapid7, the maintainers of Metasploit penetration testing tool, explains in a blog post on Tuesday that the web browser in Android 4.3 and prior has UXSS exposures.
The researcher demonstrated with JavaScript and Ruby code that response from the play.google.com domain can be generated without the appropriate XFO header.
Staying on the safe side of Android
Avoiding compromise from actors exploiting the lack of XFO support can be done by using a web browser that is not vulnerable, such as Google Chrome, Mozilla Firefox or Dolphin. Beardsley adds that being logged out of the Google account is also helpful, although this practice is highly unlikely to be adopted by most of the users.
A Metasploit module has been created for penetration testing purposes. Remote code execution is achieved by leveraging two vulnerabilities on affected Android devices.
“First, the module exploits a Universal Cross-Site Scripting (UXSS) vulnerability present in versions of Android's open source stock browser (the AOSP Browser) as well as some other browsers, prior to 4.4 (KitKat). Second, the Google Play store's web interface fails to enforce a X-Frame-Options: DENY header on some error pages, and therefore, can be targeted for script injection. As a result, this leads to remote code execution through Google Play's remote installation feature, as any application available on the Google Play store can be installed and launched on the user's device,” Beardsley explains.
 14 DAY TRIAL //
14 DAY TRIAL //