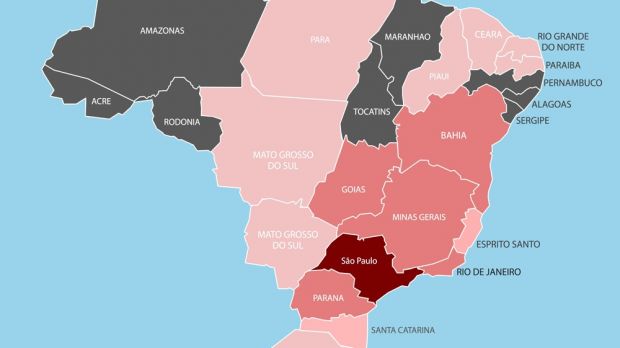
The boleto fraud continues to impact users in Brazil, with the largest number of infections being recorded in Sao Paolo, the most populous city in the country.
Regulated by the Brazilian Central Bank, boletos are a highly popular payment method that can be used both online and offline, and are accepted by a wide variety of merchants; they are created with an expiration date which can be extended by generating a new document.
Attackers change information for the money recipient
Initially, it was discovered that the crooks relied on the man-in-the-browser (MitB) technique to intercept boleto transactions and forge the details indicating the recipient of the funds.
Researchers at Trend Micro observed in the past three months a malicious email campaign designed to trick recipients into installing a malicious extension for Firefox or Chrome that would replace the payment information on an electronically generated boleto with values from the attackers.
When generating a new boleto, the browser component sends the legitimate payment details from the victim’s document to a server in a bulletproof hosting service. In exchange, a boleto with forged payment data is delivered to the victim, ensuring that the funds reach the cybercriminal instead of the intended recipient.
Users in at least 15 cities are impacted
By analyzing a malicious extension slung at Firefox users, the researchers noticed that a JavaScript file contained a regular expression pattern that matched payment slip numbers, which would trigger the malicious activity.
Another variable in the code included “138 Brazilian bank prefixes used by the extension to match a boleto number. When a bar code image is found, the malware downloads a new one from the command-and-control (C&C) server,” Trend Micro says.
The researchers observed that the highest number of infections resulting from this campaign was in Sao Paulo, but other cities in Brazil were also impacted: Rio de Janeiro, Minas Gerais, Parana, Goias, Bahia.
A lower infection rate was detected in different cities: Rio Grande do Sul, Santa Catarina, Esprito Santo, Mato Grosso, Para, Piaui, Paraiba and Ceara.
Symantec studied the boleto fraud too and determined that the operation was carried out through three main malware families - Eupuds, Boleteiro, and Domingo - which execute the theft either through the man-in-the-browser technique or the browser extension method.
Domingo can also scan the storage space on the computer searching for boleto files and modifies their payment values and identification numbers.
The malware is generally delivered to the victim via spam. Trend Micro says that the rogue messages contain fake threats for unpaid debts to the government and provide a link to the malware, which its products identify as Broban.
 14 DAY TRIAL //
14 DAY TRIAL //