Changeup, a polymorphic worm that generated more than 5 million unique variants, created a network of infected computers (botnet) that consisted mostly of systems located in the United States and South Africa, shows telemetry data from a security company.
The malware was first spotted by researchers in 2009 and gained the attention of the experts due to its aggressive spreading via mapped drives, removable storage devices, as well as ZIP and RAR archives.
To move to new targets, the threat started to leverage in 2010 the recently re-patched LNK vulnerability in Windows (CVE-2010-2568), which was also the one used in the Stuxnet cyber-espionage campaign by the Equation Group.
A little under 30,000 monthly detections recorded in early 2015
An alert from US CERT (United States Computer Emergency Readiness Team) informs on Thursday that Changeup, also known as VObfus, VBNA, AAEH and Beebone, morphs every few hours.
Its purpose is limited to downloading other pieces of malware, including banking Trojans, click-fraud programs, crypto-malware and other botnet threats.
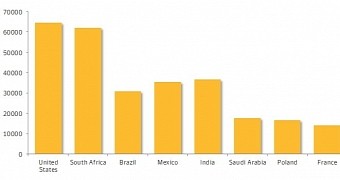
According to data received by security company Symantec from its systems throughout the world, most of the Changeup infections were in the United States, where 11% of the compromises were recorded. Following at a difference of less than 1% is South Africa.
Other countries affected by the malware are Brazil, Mexico, India, Saudi Arabia, Poland, France, and Nigeria.
Symantec says that it registered more than 55,000 Changeup detections per month at the beginning of 2014. A year later, the detection dropped to under 30,000.
Botnet down
On Wednesday, a task force formed of different law enforcement organizations in Europe and the US, as well as private security companies (Intel, Kaspersky and Shadowserver), took action to disrupt the Changeup botnet and sinkholed all its command and control (C&C) servers, thus cutting interaction with the affected computers.
Data collected by Shadowserver in an interval of about three hours on Thursday morning showed that a total of 6,894 unique IP addresses connected to the sinkholed C&C servers it controlled.
By far, most of the traffic came from Peru, from no less than 2,332 IPs. Next in line were Indonesia (584), Vietnam (521), Guatemala (503), and Kazakhstan (435).
 14 DAY TRIAL //
14 DAY TRIAL //