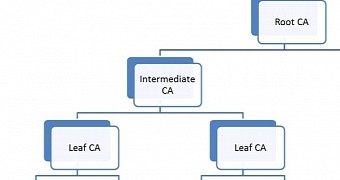
Abundant trust in an intermediate certificate authority caused certs for several Google domains, trusted by almost all operating systems and web browsers, to be issued without authorization.
It is likely that other fraudulent TLS certificates for other websites also exist, causing the risk of being misused for impersonation and thus decrypting secure communication between a client and the server through a man-in-the-middle (MitM) attack.
Public-key pinning protection works only for some websites
The incident involves Egypt-based company MCS Holdings, which acted as an intermediate certificate authority, a position granted by CNNIC (China Internet Network Information Center), the superior root certificate authority (CA).
CNNIC is present in the root stores in most operating systems and web browsers, which basically makes the bogus certificates trusted by these entities.
In a blog post published on Monday, Google security engineer Adam Langley explains that users of Chrome browser and Firefox versions starting 33 are not affected by the problem due to the public-key pinning security measure.
This mechanism has been implemented in web browsers for stronger verification of certificates based on a public key known to the host the certificate belongs to and the browser, which also has it stored. The public key is derived from a private one that is secret.
However, public-key pinning is available only for Google domains and a few other websites. At the moment, it is unclear whether certs for other domains have been issued, and which they are.
Private certificate key stored inappropriately
To mitigate the risk, Google notified CNNIC and the major web browsers about the incident, and the MCS Holdings intermediate certificate has been blocked in Chrome via a CRLSet push, a method for quick revocation of certificates in emergency situations.
The explanation received by Google from CNNIC was that MCS Holdings was supposed to issue certificates only for the domains it registered, as stipulated in the agreement and in accordance with the CA’s policies and practices.
CNNIC has revoked the intermediate certificate used by MCS Holdings to generate other fraudulent domain certs.
Furthermore, the company did not store the private certificate key properly, in a hardware security module (HSM), but in a MitM proxy (a firewall device) that allows interception of encrypted traffic (HTTPS) without raising any suspicion to the users since the web destination looks like the intended one.
“The employees’ computers normally have to be configured to trust a proxy for it to be able to do this. However, in this case, the presumed proxy was given the full authority of a public CA, which is a serious breach of the CA system,” Langley writes.
Mozilla also took steps, revocation list update expected in Firefox 37
The bottom line is that CNNIC transferred its authority, which is significant for the certificate chain of trust, to an entity that was not apt for the job, the engineer added.
Mozilla has also taken measures to maintain the safety of its users and added the revoked cert to OneCRL, its mechanism for pushing revocation data to Firefox. The updated OneCRL will be delivered in Firefox 37, due for release in early April.
Mozilla said that the intermediate cert issued by CNNIC to MCS Holdings was for testing and it had a short, two-week validity period, set to expire on April 3, 2015.
 14 DAY TRIAL //
14 DAY TRIAL //