Messages in a recently observed email campaign that delivers TorrentLocker ransomware use the DMARC (Domain-based Message Authentication, Reporting and Conformance) technical specification to trick spam filters and to return reports to the malicious sender.
DMARC relies on SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), two email validation mechanisms that are used to determine that the message is coming from a host authorized by its domain administrator and that the communication has not been tampered with while in transit.
Use of the DMARC policies are not under any restriction and they are available in the public DNS (domain name system), meaning that they can be used by both legitimate and malicious parties.
Australians are most affected
TorrentLocker is a relatively new piece of ransomware with file-encryption capabilities. It has been spotted since August 2014 and has affected thousands of users across the world; security researchers found that in one month cybercriminals were able to collect profit of about $224,000 / €200,000.
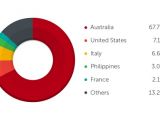
Data from Trend Micro gathered through its Smart Protection Network platform shows that users in Australia are the main target of this campaign, with an infection rate of 67.7%, starting from November 2014.
Other countries affected by the malware include the US (7.13%), Italy (6.65%), Philippines (3.09%) and France (2.14%).
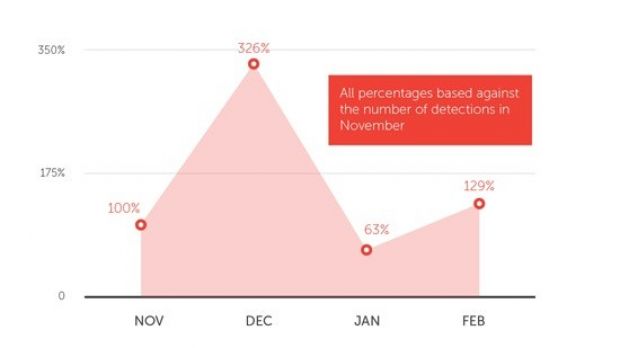
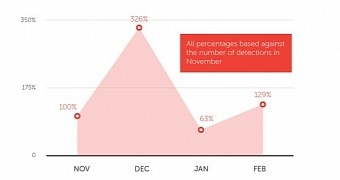
Researchers say that the campaign has its ups and downs, with a significant spike recorded in December 2014, followed by a drop in January 2015 only to pick up again in February.
Cybercriminals no longer clueless about success of the campaign
Using the DMARC specification, the crooks can receive important information about the success of the nefarious operation, which would allow them to refine the strategy and tactics for the messages to reach a wider number of potential victims.
One detail available is the amount of messages that failed to get past the SPF/DKIM verification and got quarantined or rejected, as well as the number of emails that passed.
Furthermore, they would be able to see certain data extracted from failed messages (header information and URIs in the body); this, of course, would be available only if the mail server includes support for this service.
After an analysis of the SPF and DMARC record, researchers noticed that the threat actor collected details from the rejected emails, which included the name of the Internet Service Provider (ISP), of the mailbox provider, contact information, IP addresses, and SPF and DKIM authentication results.
This is precious data that permits changing the way future spam campaigns are run, making them more targeted in order to reach a wider audience.
 14 DAY TRIAL //
14 DAY TRIAL //