A new step in the evolution of ransomware has been documented by security researchers who discovered a sample that encrypts the files on the storage unit and creates unique instances of itself due to its polymorphic feature.
This threat has been named VirRansom and VirLock by researchers from Sophos and ESET, respectively, in order to relay both its virus and desktop locking and ransomware sides. However, unlike the usual crypto-malware, this one allows decryption of the files, but it won’t stop locking the screen, thus forcing the victim to pay.
Popular files are infected
What the malware does once executed on the computer is to attach itself to a file which is then embedded in a Portable Executable (PE) and added the EXE extension, if it is not an executable.
It is worth mentioning from the get go that the threat scrambles the files it affects, but it also decrypts them upon execution, only this action comes at the expense of getting the computer infected.
The moment the user launches the infected file, the virus is automatically deployed on the system. ESET researchers say that two instances are dropped in the “%userprofile%” and “%allusersprofile%” folders. Because of its polymorphic nature, these are unique files.
According to the analysis from the antivirus vendor from Slovakia, the list of targeted files VirLock can infect includes documents (DOC, XLS, PDF, PPT), images (PNG, GIF, BMP, PSD, JPG), audio (MP3), video (MPG), and archives (RAR, ZIP).
It appears that at the moment there at least six variants of the malware circulating in the wild.
Screen is locked, important processes are blocked
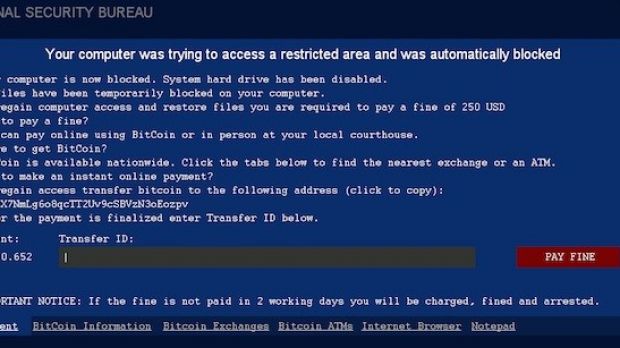
Although VirLock/Ransom does not encrypt the files the way crypto-malware does in order to coerce the victim into paying the ransom, it relies on locking the computer screen to achieve its goal.
When in lock state, the malware also kills explorer.exe and prevents opening Task Manager and other processes that could help bypass the restriction, ESET researchers say.
“The file scrambling is a secondary annoyance – a rather serious annoyance, we admit – that keeps you out of your files unless you open them directly, which then guarantees that you will become, and remain, infected,” Sophos added, contributing to the whole picture regarding the behavior of the threat.
The ransom message is a classic one, threatening with legal consequences as a result of copyright infringement allegations, unless 0.652 BTC is paid ($216 / €177).
ESET has released a standalone cleaner for this particular threat, while Sophos also provides a free tool designed to get the job done.
 14 DAY TRIAL //
14 DAY TRIAL //