A security researcher programmed a Teensy 3.0 to emulate a human interface device (HID) in order to deliver malicious files to a computer it connects to.
The experiment has the micro-controller pose as a keyboard, which also allows it keystroke input on the machine, making it all appear as if a human were typing.
Nikhil Mittal created Kautilya, an open-source tool designed for offensive security purposes, that can drop different payloads for an HID in order to gather information, exfiltrate hash dumps and intercepted keystrokes, learn WLAN keys, collect credentials, or dump process memory and Windows Vault credentials.
Payload executes commands and scripts using PowerShell
Not long ago, the researcher added a new function that permits delivering malware to the system. Mittal included support for retrieving and executing Word and Excel documents, CHM (Compiled HTML Help) items, shortcuts (LNK) or JAR files.
The Microsoft documents can be laced with malicious macro scripts that can be used to funnel in information from a remote location. “The Word file contains an auto executable Macro which executes when the document is opened. PowerShell commands and scripts could be executed,” the researcher said in a blog post on Tuesday.
A weaponized CHM file has to be generated on the attacker’s machine, where it is compressed into a ZIP archive and then byte-encoded. With the file written to the HID as a byte array, it can then be dropped on the target machine.
Mittal warns that the byte array is large, and typing it on a target takes longer than in the case of other payloads; the same occurs with JAR payloads.
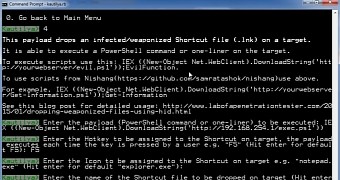
LNK payloads can be assigned hotkeys
In the case of LNK files, a shortcut path is defined to the command-line application. The command or script to be executed is passed as an argument. The researcher notes that, if a hotkey is assigned, the shortcut launches every time the user presses the right combination.
“When the HID is connected to a target. A shortcut is created on the current user's desktop. Whenever a user clicks on the shortcut or presses the hotkey the specified command or script would be executed,” Mittal explains.
A video presenting Kautilya’s new functionality has been created by the researcher and posted on YouTube. It shows how Microsoft Word documents can be dropped on a target machine with the keyboard functionality of a programmable HID.
 14 DAY TRIAL //
14 DAY TRIAL // 