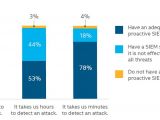
Time is essential when fighting back targeted attacks, and a recent study showed that most of the businesses relying on a SIEM (security information and event management) solution were able to defend against a targeted attack and managed to detect it in minutes.
SIEM products are designed for proactive attack prevention and provide real-time analysis of security events on the infrastructure; they can collect, store, analyze and report log data that can also be useful in the forensic investigation of an incident. Real-time SIEMs can also automate actions triggered by specific events.
Most businesses with SIEM spot an attack in minutes
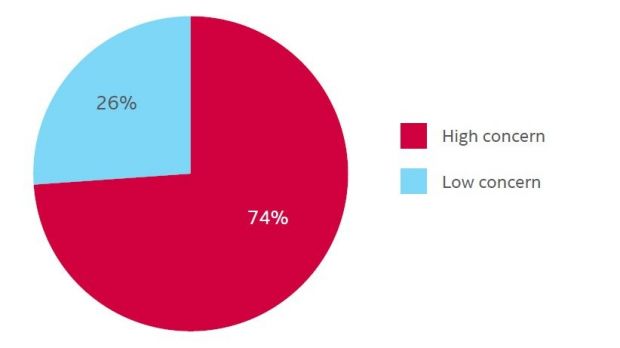
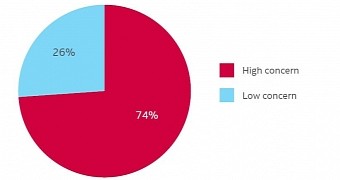
A survey conducted by Evalueserve in August and sponsored by McAfee, reveals that 74% of the respondents have high concerns about targeted attacks and advanced persistent threats.
The total number of respondents is 474 and includes top management individuals at companies with more than 50 employees, from the US, UK, Germany, Australia, and France.
According to the research (When Minutes Count), the worries stemmed from direct experience with this type of incidents, as more than half of the companies with 50 employees and above faced at least ten targeted attacks in the previous year.
However, most of those saying they have little concern about such attacks had real-time SIEM protection in place. Moreover, thanks to this solution, a large number of them benefited from a faster incident response time.
IT administrators can set up rules for filtering out uncommon events and investigate them in order to determine if actions precursory to an attack are involved.
Indicators of a targeted attack
The report from McAfee provides a set of eight indicators of attack companies should take into consideration.
Communication with a foreign country that is not connected to the business and traffic to a known bad destination are the most obvious signs of malicious activity; and so is communication outside the network through non-standard protocols or sending of command shells instead of HTTP traffic using port 80.
Signs of an attack also include detection of malware outside standard business hours, at night or on weekends. On the same note, repeated re-infection of a host after cleaning indicates targeted activity through a rootkit or other type of persistent malware.
Lateral movement in the network is announced by network scans from an internal host that communicates with multiple machines in a short time frame. Once inside the target network, cybercriminals try to analyze the infrastructure to find weak spots for deeper intrusion.
Alarms from a single host, along with duplicate events from several systems in the same network during a 24-hour period, could indicate attempts of intrusion.
Authentication attempts to or from different geographic regions from the same account is also an obvious reason for concern.
Setting up rules for detecting these events could help an organization spot a targeted attack in time and prepare defensive actions.
 14 DAY TRIAL //
14 DAY TRIAL //