Cybercriminals have started to take advantage of the YouTube Partner Program to fill their pockets and infect computers with a click-fraud malware called Tubrosa that generates artificial views to videos they post on YouTube sharing platform.
The threat is delivered via malicious emails carrying the threat in the attachment, which, when opened, leads to infecting the computer system.
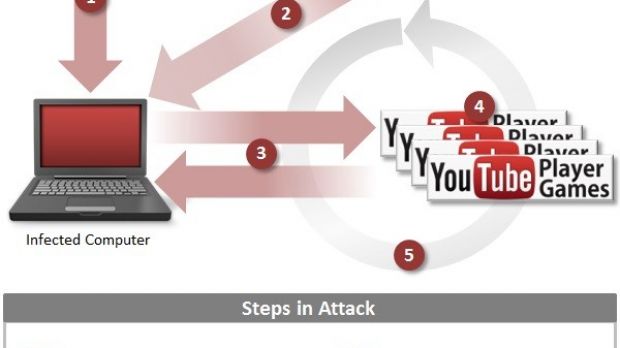
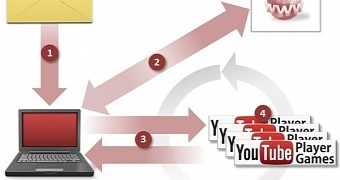
Security researchers have observed that it is a two-stage attack, the second part consisting in downloading a list of about a thousand YouTube links pointing to the scammer’s videos.
PHP scripts used to bypass YouTube verification mechanism
YouTube Partner Program allows the owner of a channel to monetize from their content by cashing in revenue from advertisements.
According to Symantec, Tubrosa is equipped with a module that bypasses the verification mechanism used by YouTube Partner Program to determine if the view count of a video is inflated artificially or not.
However, the malware relies on two PHP scripts to change the referrer and the user-agent, which contain information about the origin of the viewer. By running these scripts, the malware ensures that the information reaching YouTube about the viewer is not the same, thus making it look as if different viewers access the videos.
As per Symantec’s analysis, Tubrosa launches the links to the clips on the compromised computer in the background and it “will lower the volume of the compromised computer’s speakers to zero.” This way, the user is unaware of the fraudulent activity and only notices that something is wrong when the machine’s resources are maxed out, resulting in significant performance loss.
Cybercriminals earned thousands of dollars
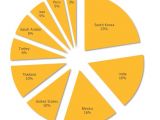
It seems that the distribution of the malware started in August 2014, as soon as the crooks uploaded their video copies. Telemetry information from the security company shows that most of the machines affected by this threat are located in South Korea (26%), India (16%) and Mexico (16%).
Other countries where it has been observed include the US (10%), Thailand (10%), Turkey (6%) and Saudi Arabia (6%).
The researchers say that they have not seen the malware being sold on underground forums, which would indicate that it is employed for the benefit of a single cybercriminal group.
Although it has been operating for a while and the number of views added fraudulently to the videos amounted to more than two million by the end of 2014, Symantec estimates that the business generated a few thousand dollars.
 14 DAY TRIAL //
14 DAY TRIAL //