A new piece of malware discovered by security researchers has been found to allow an attacker to authenticate on Microsoft Active Directory (AD) systems as any legitimate user, with a password of their choice.
The threat has been named Skeleton Key and it was encountered on AD systems that relied on single-factor authentication (SFA), which basically uses only a username and a password.
There is no persistence, malware resides in memory
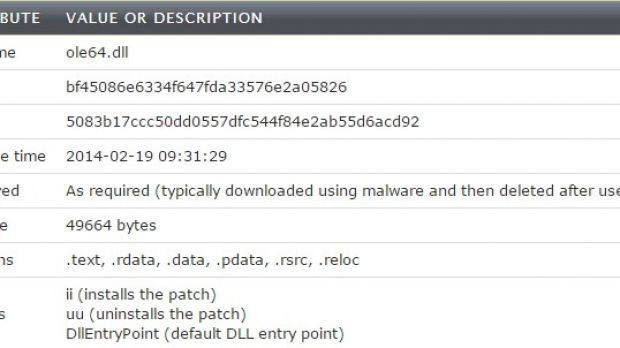
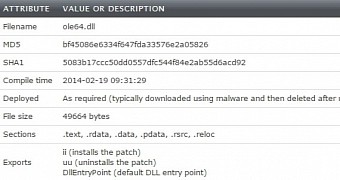
Researchers at Dell SecureWorks Counter Threat Unit (CTU) analyzed the behavior of the malware and observed that it was deployed as an in-memory patch on a victim’s AD domain controllers.
Because it resides in the memory of the system, no persistence is achieved and the infection cycle needs to be re-initiated when the machines are restarted.
Apart from Skeleton Key, the researchers discovered no evidence of other malware, which would suggest that the threat actor infers that the infected servers have been rebooted only when they can no longer authenticate; alternatively, they may have planted a remote access Trojan on a different machine that re-deploys the malware to the Active Directory server.
It is important to note that the threat requires domain administrator credentials in order to be executed. “CTU researchers have observed threat actors deploying Skeleton Key using credentials stolen from critical servers, administrators' workstations, and the targeted domain controllers,” they said in a blog post on Tuesday.
Skeleton Key runs on 64-bit systems, relies on domain admin credentials
The sample caught by Dell’s security experts led them to the discovery of an older variant on a different machine, used to compromise others, called “jump host.”
Upon analyzing the malware strain, it has been discovered that the malicious file moves from a staging directory on a jump host on the network. Then, relying on a set of stolen domain administrator credentials, it tries to access administrative shares on the domain controller.
A fallback plan is available if the log-in data does not work, and it consists in using password stealing utilities to obtain the information in plain text from certain locations, such as workstations, memory of another server, or targeted domain controller systems.
Once valid credentials are obtained, Skeleton Key is copied on the targeted machine and executed. In the final stages of the compromise, traces are removed by deleting the malware from the persistent storage of both the infected machine and the jump host.
It appears that the malware only runs on 64-bit versions of Windows, and according to the investigation results, there is the possibility that it affects other organizations apart from the client the security researchers assisted with cyber incident response work.
 14 DAY TRIAL //
14 DAY TRIAL //