A new variant of Simplocker, the first file-encrypting ransomware for Android devices, has been discovered, and it relies on unique encryption keys for infected devices, security researchers have found.
First spotting of the malware came in 2014 from ESE and Kaspersky. Although multiple versions circulated in the wild, all of them were powered by crude code and encryption methods that allowed security researchers to come up with an antidote in a very short time.
Malware poses as Flash Player app
The latest revision, on the other hand, seems to be an evolutionary step, according to researchers from Avast, who found that devising a solution to revert the encryption effect is no longer an easy task.
Over 5,000 unique users have been infected just a few days after the new strain was detected.
Previous versions of the malware relied on a single key to lock files on the affected devices.
"The new variant however, locks each device with a 'different key' which makes it impossible to provide a solution that can unlock each infected device, because that would require us to 'make copies' of all the different 'keys,'" Nikolaos Chrysaidos from Avast says in a blog post.
Spreading Simplocker is done through the common method of disguising it as a legitimate program for the mobile platform.
According to the researchers, the malicious sample poses as an installation for Flash Player. It looks like the cybercriminals deliver advertisements that inform the potential victim that Flash needs to be updated, pointing them to the malicious location.
In order to install the fake update the Android device needs to be configured to allow installation of software from untrusted sources, a state common to many terminals since their owners often turn to because they install programs from third-party marketplaces.
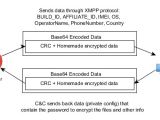
Communication with C&C is done via XMPP
As per the analysis from Avast, the malware requests administrative privileges, ensuring that it is more difficult to remove from the device because not all users know where on the phone the apps with administrator rights on the device can be disabled.
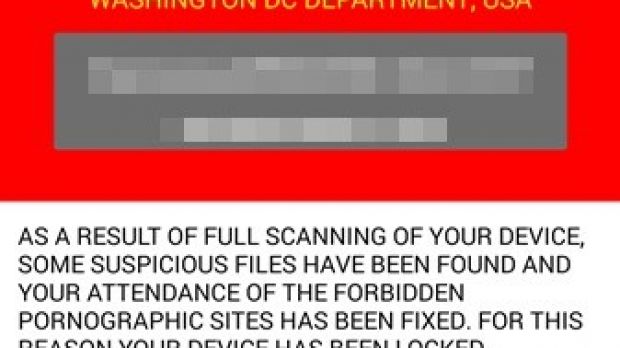
The ransom message claims to be a notification from the FBI about suspicious files that infringed copyright found on the device. As a result, the data is encrypted and can be unlocked if a $200 / €176 fee is paid.
The security company determined that the current version of Simplocker connects to the command and control server every hour using the XMPP communications protocol (username "timoftei" is used, indicating an attacker from Eastern Europe). At first contact with the server the malware sends data such as IMEI, version of the operating system, carrier name, phone number and country.

 14 DAY TRIAL //
14 DAY TRIAL //