A ready-made kit that allows anyone with minimum technical skills to build their own version of crypto-malware has become available on an underground forum, at no other cost than a piece of the ransom paid by the victims.
Malware-as-a-service is a booming business and up until recently it did not apply to ransomware with file encryption features, but this changed last week, when a toolkit called Tox was released, free of charge.
It allows anyone to quickly create ransomware that can be distributed via spam botnets or bulk email clients, charging 20% of whatever the victim pays, in exchange for the services provided by the Tox site.
Toolkit facilitates creation of crypto-malware
Security researchers at Intel Security’s McAfee Labs, found the service on the TOR anonymity network on May 19 and observed that two days later its operators updated the UI design and the FAQ documentation.
“Ransomware, though very prevalent, has not yet appeared in force in easy-to-deploy kits,” they say in a blog post; but things are likely to change because of the malware-as-a-service business approach.
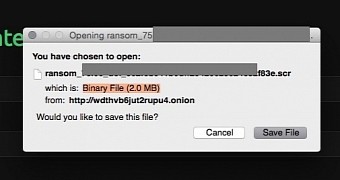
All cybercriminals have to do is register for the service, and create their version of ransomware via an automated process that requires providing the ransom amount, captcha and a message of their own, which is optional. The resulting file is a 2MB large executable SCR file.
The web-based administration panel shows the number of infections, how many victims paid the ransom fee and total profit. The money is paid after supplying a bitcoin wallet address and the service takes its cut.
Tox ransomware uses readily available tools for encryption
Malware analysts say that the malware piece created this way is not complex and lacks efficiency in the code, signaling less-skilled developers, as they left behind identifying strings that make analysis easy.
The ransomware is compiled in MinGW and relies on AES algorithm to encrypt the files on the infected computer, using the Crypto++, free C++ class library of cryptographic schemes, with support for public-key cryptography.
The encryption key is generated with Microsoft’s CryptoAPI, which includes support for both public-key and symmetric key cryptography.
“We don’t expect Tox to be the last malware to embrace this model. We also anticipate more skilled development and variations in encryption and evasion techniques,” the researchers warn.
 14 DAY TRIAL //
14 DAY TRIAL //