New information has emerged about Ramnit, a worm turned financial malware, detailing among other things that it sported a module that turned off the protection of built-in Windows security features.
Ramnit has created a large network of infected computers that has been disrupted recently by a joint operation led by Europol with the concert of Symantec, AnubisNetworks and the security division at Microsoft.
The number of compromised machines has been established at 350,000 by Symantec, while Microsoft’s telemetry data indicates that more than half a million systems have been infected in the past six months.
Ramnit has been around since at least April 2010, when it was marked a worm that infected EXE, SCR, DLL and HTML files. It evolved into financial malware when the code for Zeus banking Trojan was leaked online.
Over 300 antivirus products are targeted by Ramnit
The Redmond-based company says that the version of Ramnit they’ve seen infecting 500,000 computers could disable Windows Firewall, the Windows Update mechanism, Windows Defender antivirus solution (built-in in Windows 8 and above) and the User Account Control security technology.
This functionality is available in the installer of the malware, so the victims’ systems would be stripped of the default protection provided by Microsoft as soon as they got compromised.
More than this, as per Microsoft’s analysis, when the connection with the command and control (C&C) server would be established, the malware would receive a list with over 300 antivirus solutions, whose processes Ramnit attempted to terminate.
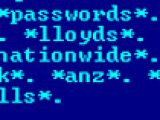
The list includes products from Avast, Bitdefender, ClamWin, Kaspersky, McAfee, ESET, Symantec, Outpost, Qihoo, Comodo, F-Secure, and F-Prot.
The module containing the list is dynamic in nature and could be updated with new entries. It was spotted for the first time in 2013, under the name “Antivirus Trusted Module v1.0.”
Malware connects to two C&C servers for different purposes
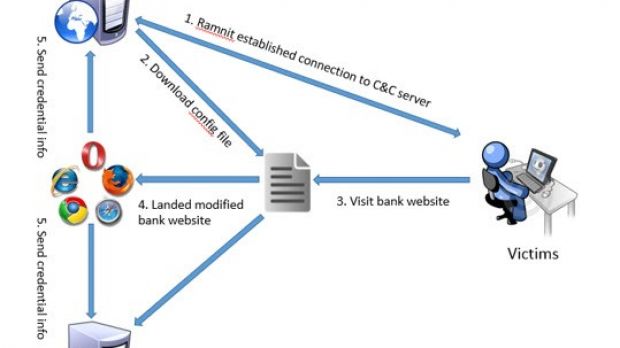
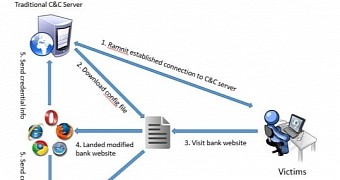
In their investigation, Microsoft researchers noticed that Ramnit relied on two C&C servers. One of them is contacted through the DGA (domain generation algorithm) and is used to deliver different components, as well as for providing remote access to the compromised machine.
The second one has the address in the configuration file and its purpose is to deal with the web injection activity for stealing online banking credentials.
To achieve its goal, Ramnit hooks into the web browser and monitors user activity until a targeted website (most of them belonging to banks) is loaded. It can then intercept the log-in credentials, as well as alter the web pages in real time, in order to trick the user into divulging sensitive information that would help the attacker gain control over the account.
Everything looks legitimate to the user since the content appears to be from the servers of the bank itself.
 14 DAY TRIAL //
14 DAY TRIAL //