A cross-site-scripting (XSS) vulnerability has been discovered in the WP Statistics component for WordPress, allowing a potential attacker to execute commands in the administration panel.
The type of the XSS glitch is persistent, also called “stored,” which means that the malicious code stays on the web server and victims receive the malicious script when requesting the information (such as entries in a database).
Sucuri made the discovery in the WordPress plug-in and disclosed it privately to the developers, prompting them to release version 8.3.1 in order to fix the problem.
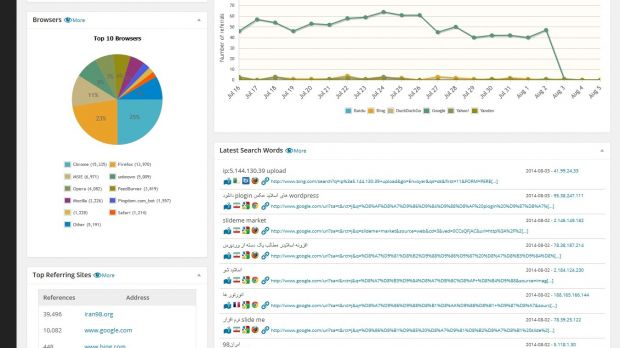
With WP Statistics (total download count is well over 800,000), website administrators have access to details about the visitors (total count, current visitors, geoIP), most visited pages or search queries, and redirects from search engines.
Statistic data controlled by the user is not properly sanitized
All websites currently running a version lower than the recently released one are vulnerable.
“An attacker can use Stored Cross Site Scripting (XSS) and Reflected XSS attack vectors to force a victim’s browser to perform administrative actions on its behalf. Leveraging this vulnerability, one could create new administrator account[s], insert SEO spam in legitimate blog posts, and a number of other actions within the WordPress’s admin panel,” Marc-Alexandre Montpas says in a blog post.
Due to the severity of the bug, no technical info has been provided by the company at the moment; details about the flaw are to be presented in about 30 days. However, Sucuri says that the issue derives from the fact that the plug-in fails to sanitize data controlled by the user and received by the website for statistical purposes.
“If an attacker decided to put malicious Javascript code in the affected parameter, it would be saved in the database and printed as-is in the administrative panel, forcing the victim’s browser to perform background tasks on its behalf,” the researcher says.
Admins should also update their WordPress version
WP Statistics 8.3.1 is compatible with the latest WordPress version, 4.0.1, which was released on Thursday to fix multiple security vulnerabilities, among them a critical XSS weakness that affects all builds before 4.0 (85.5% of all installations).
Exploiting the flaw would allow an attacker to execute malicious JavaScript code that could be used to create additional admin accounts. The code is sent through the comment field of the website.
All commands in the script are executed with administrative privileges when the malcrafted comment is viewed in the management console of the content management system.
 14 DAY TRIAL //
14 DAY TRIAL //