The legitimate use of Pastebin is currently being taken advantage of by hackers to upload malicious code to compromised websites in order to maintain continued access to them.
After getting unauthorized access to a website, cybercriminals work their way to keeping the asset under their control and create a backdoor that allows them access even if the vulnerability that was exploited in the first place receives a fix.
Pastebin is designed for code sharing
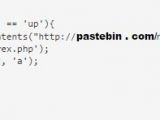
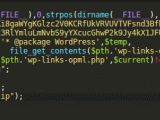
Most of the times, the backdoor code is hosted on a remote server, but in some recent attacks that leverage a security flaw in Slider Revolution (RevSlider) plug-in for WordPress, the hackers rely on Pastebin to store the malicious code.
“Technically, the criminals used Pastebin for what it was built for – to share code snippets. The only catch is that the code is malicious, and it is used in illegal activity (hacking) directly off of the Pastebin website. Pastebin.com allows users to download the code in ‘raw’ format,” said in a blog post Sucuri’s Denis Sinegubko.
However, the functions available in the code are not available in clear text and hackers often use an encrypting tool designed to work with Pastebin. When the decoding function is executed, the script becomes ready for use.
Vulnerability has been patched since February 2014
The glitch in RevSlider caught the attention of Sucuri website security company in early September 2014. At that time, the systems of the company recorded that cybercriminals attempted to trigger the vulnerability in more than 1,000 websites.
In December 2014, a new wave of compromises followed, with malicious code being served from soaksoak.ru website, which was flagged by Google as a dangerous location.
All these attacks occurred despite the fact that the developer of RevSlider issued a patch to eliminate the flaw in February 2014.
However, the automatic push of the new version was done only to customers who purchased the WordPress component directly through their store. Anyone getting the plug-in from a different reseller had to apply the update manually.
As such, many websites relying on RevSlider to improve how content is displayed through slides with different transitions and effects remained vulnerable. Moreover, a large number of theme authors included it in their work without enabling an update for it.
Admins should make sure that the latest version of RevSlider is running on their website in order to avoid intrusions.

 14 DAY TRIAL //
14 DAY TRIAL //