The website of Internet Systems Consortium, ISC.org, which maintains BIND, one of the most popular DNS software on the Internet, has been hacked and is currently down, warning visitors who accessed it recently to check their computers for malware.
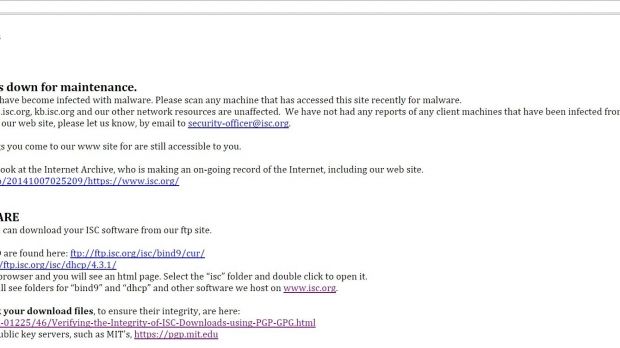
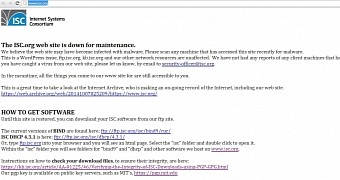
Its administrators pulled the site offline as they are still trying to work things out and clean malicious code. “We believe the web site may have become infected with malware. Please scan any machine that has accessed this site recently for malware,” says the main page at the moment.
Drive-by download attack risk
The website relies on WordPress and it appears that the problem is with the CMS (content management system), so it was not an attack specifically aimed at ISC.org and its resources.
It appears that the perpetrators have managed to modify the main page of the site so that visitors are redirected to a malicious location hosting Angler Exploit Kit (EK), which integrates exploits for multiple software pieces.
“In this case we observed IE, Flash and Silverlight exploits. If exploitation is successful, the exploit will continue to download and execute a malicious binary in-memory,” said McEnroe Navaraj of Cyphort, a company that created a product for proactive detection of cyber incidents.
Cyphort researchers analyzed the infection scheme and observed that the user was served the exploit kit after multiple redirects. They determined that a vulnerability, tracked as CVE-2013-2551, in Internet Explorer 6 through 10 is exploited.
ISC software has not been affected in any way
Before dropping the payload and installing it, the exploit first checks if the Internet Explorer version is a vulnerable one by enumerating the plugins it has installed and their versions.
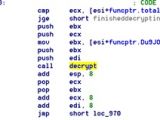
If the computer can be compromised, the malicious binary is downloaded and executed. There is no information on the type of threat launched on the victim’s computer, but most of the times it is a dropper that connects to a different location to download malware specialized in stealing sensitive information, banking log-in data in particular.
However, the researchers have discovered that the payload is not stored on disk but loaded directly into the memory of the computer. Poweliks Trojan is known to work this way, which makes it quite difficult to detect.
Internet Systems Consortium informs that infecting their website presents no risk to BIND DNS or the ISC DHCP tools they develop, because these are stored on a separate server.
Furthermore, the software is cryptographically signed and its integrity can be verified by using the public keys available in its download section.
WordPress and components built for it are a constant target for cybercriminals who take advantage of the popularity of the platform to make as many victims as possible.
 14 DAY TRIAL //
14 DAY TRIAL //