A new piece of malware is currently used by threat actors in a targeted attack to gather information about the victim and upload the data to Google Drive.
Named Drigo, the Trojan starts searching for a specific set of files in certain locations on the hard drive, and it exfiltrates them to a Google Drive storage location.
The attackers are selective in the file formats they look for and restrict their search to XLSX, XLS, DOC, DOCX, PDF, TXT, PPT and PPTX files present in locations like Recycle Bin and the Documents folder, but other directories are also scoured.
After analyzing the malware, threat analyst Kervin Alintanahin from Trend Micro discovered that the actors behind it relied on the OAuth protocol for authentication. For this, they hard-coded the client_id and client_secret strings along with a refresh token to keep the OAuth access token from expiring.
According to the researcher, the documents uploaded to Google’s cloud revealed the names of the entities targeted by the bad actors and most of them were government agencies.
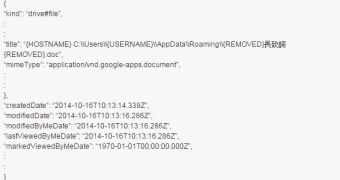
From the name of one of the documents, it appears that the victims are located in China. Alintanahin said that, on Tuesday, files extracted from victimized computers could still be seen in the attacker’s online storage.
Based on the observations during the investigation, it appears that the malware is capable of just uploading documents to Google Drive, an activity that is most of the times consistent with reconnaissance missions.
“After all, one of the key aspects in a successful attack is having enough information on the target. The more information they can gather, the more vector of attack they can use on their target,” notes Alintanahin in a blog post for Trend Micro.
 14 DAY TRIAL //
14 DAY TRIAL //