A vulnerability found in Dropbox SDK for Android can be exploited by an attacker to cause apps using the software development kit for Dropbox synchronization to upload the data to an unauthorized account.
Security researchers warn that the flaw can be exploited through a malicious app installed on the mobile device or remotely, through drive-by attacks.
However, the attack is not successful if the Dropbox app is installed on the mobile device, even if it is not configured, because the app needs to be registered on the Dropbox website.
Attack scenario
Roee Hay and Or Peles from IBM Security Systems developed an exploit for the vulnerability, dubbed DroppedIn, that affects Dropbox SDK 1.5.4 through 1.6.1. The issue has been mitigated in build 1.6.2 of the development kit four days after the private disclosure made by the researchers.
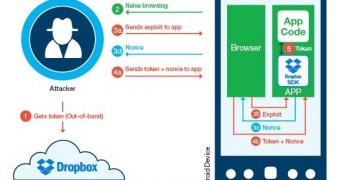
Identified as CVE-2014-8889, the vulnerability allows an attacker to steal the nonce parameter, which is generated by the SDK and delivered to the Dropbox server to validate an authorization request for a third-party app to access the content in the cloud.
In the attack scenario created by the two researchers, the cybercriminals need an access token associated to their account and the attacked app.
“This is especially easy because attackers can simply download the app to their device, authorize it on their Dropbox account and record the returned access token pair,” Roee Hay says in a blog post on Wednesday.
Next, the victim is directed to a malicious website which delivers the exploit and forces the nonce to be delivered to a rogue server controlled by the attackers.
With the session’s nonce in hand, the cybercriminals can inject their own token into the app and thus link it to their Dropbox account. From then on, any information synced by the app is actually delivered to the attackers’ Dropbox account.
Vendor's response was prompt
The vulnerability was disclosed to the cloud storage service provider on December 1, 2014, and a patch became available four days later.
The researchers tested their proof-of-concept with 41 apps that use a faulty version of Dropbox SDK and found that 31 of them were vulnerable to the DroppedIn attack, as they relied on SDK releases 1.5.4 through 1.6.1.
Among them were Microsoft Office Mobile and 1Password, which are highly likely to hold sensitive information.
At the moment, the latest revision of Dropbox SDK for Android is 1.6.3, released on January 9, 2015. Developers are urged to update as soon as possible and patch their applications.
Demonstration of the attack:
 14 DAY TRIAL //
14 DAY TRIAL // 