A solution that recovers credentials from different programs can be employed by both cybercriminals and legitimate users that forgot their passwords. LaZagne is an open source project aimed at the second category but with a potential to be used for nefarious purposes, too.
The tool is a collection of Python scripts that decode the files used by programs to store passwords, relying on resources readily available either on the operating system or externally.
Extract info from KWallet and LSA secrets
LaZagne works on both Windows and Linux operating systems and includes support for popular programs that store passwords (22 on the former and 12 on the latter). More than this, it is suitable for retrieving the credentials for WiFi connections.
Developer Alessandro Zanni published the project on GitHub, complete with usage instructions and a guide for creating a custom password recovery script.
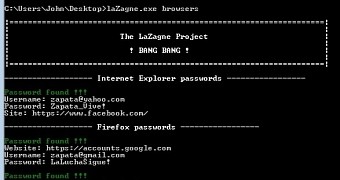
There are multiple modules available, each loaded via the command line interface, specific for the type of programs targeted: web browsers (Google Chrome, Mozilla Firefox, Internet Explorer), chat clients (Pidgin, Skype, Jitsy), email clients (Outlook, Thunderbird), FTP clients (FileZilla, WinScp, CoreFTP) or databases (Squirrel, DBvisualizer, SQL Developer).
Although only 12 programs are listed as supported on Linux, LaZagne can parse files from GNOME Keyring and KWallet password manager, which are used for storing passwords for programs that integrate with them on GNOME and KDE systems.
On Windows, it can reach LSA (Local Security Authority) secrets area, which stores service account passwords, EFS encryption keys, logon credentials or the key for remote desktop protocol sessions.
Custom modules can be added
The set of modules currently available in LaZagne can be expanded by the user with custom scripts targeting password recovery from a specific application. Zanni makes available the code standards that need to be met for the script to work.
The tool is aimed at IT professionals as an easy solution for retrieving lost passwords, but it can also be integrated as a module of a nefarious project with the purpose of exfiltrating sensitive information from user’s computer.
 14 DAY TRIAL //
14 DAY TRIAL //