eNom domain registrar informed its customers on Thursday that it was the victim of a group of attackers, who altered the domain name system (DNS) settings of four domains, redirecting traffic to different web resources than those intended by the owners.
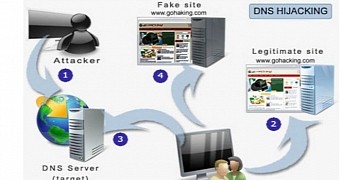
DNS configuration includes defining the IP addresses for the name servers, which are used to translate a domain name into the IP address corresponding to the web server that hosts it.
By changing these settings, cybercriminals can point visitors of a legitimate website to a malicious location that could be used to serve malware or to impersonate the original content with the purpose of collecting user information, such as login credentials.
Attackers redirected traffic for a short while
Taryn Naidu, CEO of eNom, says in the letter to the customers that the group carried out “what appears to be a very sophisticated attack,” and that apart from the traffic redirect, there is no evidence that the attackers accessed any sensitive information.
Following an investigation into the incident, the company concluded that no domain names were stolen and customer accounts and information were not accessed.
According to Naidu, the incident was discovered quickly and federal law enforcement was contacted within hours from the attack.
“This attack hijacked the DNS traffic of 4 domains for a very short period of time before we mitigated the situation,” he wrote to customers. The letter had no other purpose than to show the company’s effort for transparency.
St. Louis Federal Reserve reported traffic hijacking incident
On Monday, St. Louis Federal Reserve alerted its customers that hackers managed on April 25 to breach an undisclosed DNS vendor it used, and modified the IP addresses of name servers, causing visitors to reach a fraudulent web page.
The institution’s domain registrar is eNom, which would indicate that the two incidents are related. However, one could only speculate on this because eNom does not mention the date of the breach, nor does it name the domains that have been affected by the attack.
The only connection between the two events is currently the timing for the disclosure. eNom's full letter to customers is available below.
 14 DAY TRIAL //
14 DAY TRIAL //