Cybercriminals have directed their attention towards architecture firms in Denmark, adapting their tactics to lure employees of a select number of them to download a remote access Trojan (RAT) known as DarkComet.
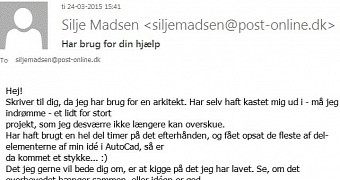
The bait is delivered through spear-phishing, using a message that is written in perfect Danish, researchers say.
The DarkComet RAT is a free piece of malware widely known in the security industry because it is often used for nefarious purposes, although its author, a French programmer, advertises it as a remote access tool, a legitimate application that provides a high level of control over a network of computers.
Targeted attack, hefty suite of functions identified
Security researchers at Danish security organization CSIS found that a group of cybercriminals tailored the content of the malicious email to be of interest to particular architecture companies, inciting the recipient to download a file that purports to be generated by AutoCAD 2D and 3D design software.
The item is stored in a Dropbox account and once downloaded and executed, it automatically begins collecting and exfiltrating data from the compromised system.
Apart from this, the threat also features functions like keystroke capture, stealing data from the clipboard, taking screenshots, activating the webcam and the microphone, or setting up a remote desktop session. From the initial analysis, CSIS experts have determined that the malware piece is DarkComet.
Cybercriminals are not at the first spear-phishing attempt
To mask the compromise, the threat shows a dialog that informs the victim that a DLL file is missing, tricking them into believing that the project file is damaged and does not work. However, this is enough for DarkComet to deploy its malicious routines in the background.
During their analysis, the experts found that the command and control (C&C) server used by the cybercriminals to communicate with DarkComet was located at an IP address in Canada.
Last week, CSIS reported that a phishing operation was targeting chiropractors in Denmark, delivering a ransomware with file-encryption capabilities its author(s) called PacMan.
They determined that both chiropractor offices and architecture firms in the country were attacked by the same group of individuals.
 14 DAY TRIAL //
14 DAY TRIAL //