Just as GitHub service recovered completely from the massive distributed denial-of-service (DDoS) assault that started on March 27, new evidence emerges implicating the Chinese government in the incident.
Researcher Robert Graham from Errata Security built a custom traceroute tool showing that a man-in-the-middle (MitM) device located on the backbone of service provider China Unicom was responsible for altering replies to requests coming to China from other parts of the world.
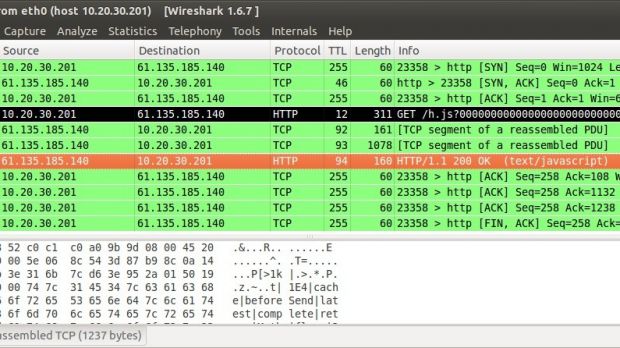
The modification consisted in replacing the JavaScript code for Baidu Analytics with one that would constantly reload two specific pages on GitHub, providing access to Google searches (GreatFire) and the New York Times publication in areas where the locations are prohibited.
Packet route shows position of MitM device
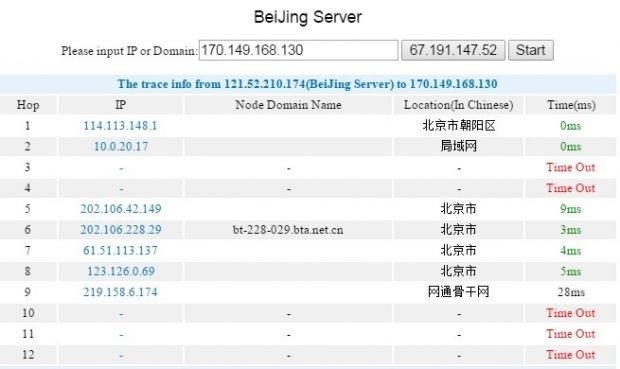
The TCP packets sent by Graham to the Baidu server started with a TTL (time-to-live) value of 64 and the server returned a value of 46, meaning that there were 18 hops/nodes on the path. However, in the case of web requests, the TTL values were higher, suggesting an intermediary along the way.
With his custom traceroute tool, Graham first initiated a connection with normal TTLs to the Baidu server so that the destination was reached; but when the web request packet was sent, a smaller TTL would be used “so it would get dropped before reaching the server - but hopefully after the man-in-the-middle saw it,” the researcher wrote on Tuesday.
Altering the TTL value of the packets eventually led to establishing the position of the MitM device that injected the malicious JavaScript.
China's Internet censorship tool is on China Unicom's infrastructure
Since packets trigger a response from the router they reach, which includes the sender’s IP address, the researcher was able to create a map with the routers between the origin and the destination of the packet.
“I found that the device lurks between 11 and 12 hops. The web request packets sent with a TTL of 11 are not seen, while packets with TTL of 12 are,” Graham said.
After analyzing the IP addresses in the traceroute and determining that the MitM device was on the backbone of China Unicom, the researcher ran the same experiment in the opposite direction, to the blocked address of New York Times.
This revealed that the Great Firewall ran inside the service provider’s infrastructure.
China denies involvement in the attack
On March 31, Swedish software vendor Netresec published an analysis of the TTL fields of the modified Internet packets, demonstrating that the Great Firewall of China, the active and passive network infrastructure used in China for Internet censorship purposes, was actually employed to carry out the DDoS attack against GitHub.
In response to accusations that China was behind the GitHub attack, the country's Foreign Ministry spokesperson Hua Chunying said that "it is quite odd that every time a website in the US or any other country is under attack, there will be speculation that Chinese hackers are behind it. I'd like to remind you that China is one of the major victims of cyber attacks."
 14 DAY TRIAL //
14 DAY TRIAL //