A piece of ransomware with file encryption capabilities called Locker enters into a sleep state after compromising a computer and activates at a certain time, defined by the attacker.
This approach has not been encountered with other malware of the same type, and it is unclear why the attackers delayed the encryption process for the victim’s files.
One explanation would be that they distributed the ransomware before setting up the infrastructure for storing the file decryption keys and delivering them to the victims who paid the ransom.
By adopting this method, the crooks also make it difficult to trace the time of infection and the delivery channels, which may range from spam email pointing to a malicious location hosting the Locker or drive-by attacks relying on malvertising and compromised websites.
Decryption key said to be destroyed past May 28
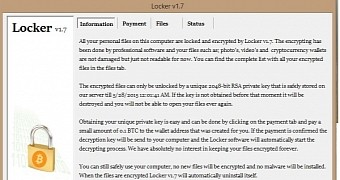
According to an analysis from Bleeping Computer, files on computers infected with Locker started to be encrypted on May 25 at midnight (local time). Unlike threats of the same kind, Locker did not change the extension of the affected items and they would appear untouched until the user launched them.
The malware deletes the copies created by Windows Shadow Copy service, but only on the system drive. This would suggest that the attackers aimed Locker at the most important data since it is common practice among users to store important files on the system volume.
On the bright side, this also means that items available on any other partition can be recovered. Furthermore, there are reports that deleting the shadow copies is not always successful and the data can be restored with special software.
After encrypting all the data (mostly documents and images), Locker displays the ransom message, demanding 0.1 bitcoins ($24 / €22) in exchange for the decryption key stored on a server hidden in TOR anonymity network.
The deadline for paying the fee was set for May 28. The message states that the decryption keys are destroyed after this date, making data unrecoverable.
 14 DAY TRIAL //
14 DAY TRIAL //