The ransomware Crowti/CryptoWall with file encryption capabilities has been seen more often in the past month on computers located in the United States, as a result of multiple new email campaigns distributing the threat.
The modus operandi of the malware should be well known by now: after compromising the system, Crowti/CryptoWall starts encrypting the data on the hard drive and then shows the victim a message asking for payment in return of a key that would unlock the files.
Thousands of users affected on a daily basis
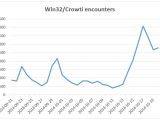
Telemetry data from Microsoft shows that Crowti activity has spiked since October 13, peaking at more than 4,000 computers infected on October 17.
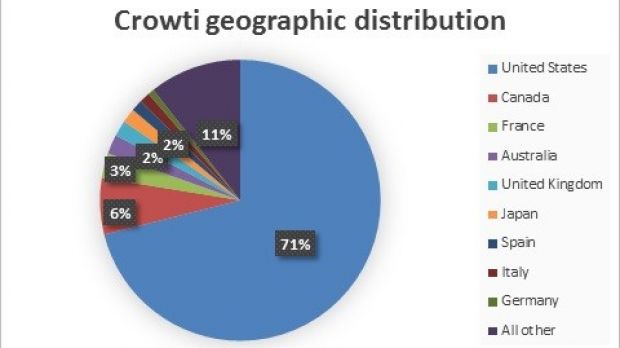
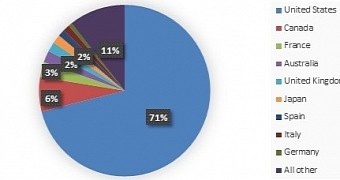
The researchers determined that most of the compromises attributed to this piece of malware in the past month occurred in the United States, where 71% of the total infections have been recorded.
Other countries affected are Canada, France, Australia, the United Kingdom, Japan and Spain, but detections were significantly lower, each region recording 6% or less of the Crowti incidents.
Malware delivered through multiple methods
Distribution of the ransomware is carried out through spam email with malicious attachments posing as documents (invoices, faxes, complaints, reports) or missed call messages.
“Our telemetry and research shows that Win32/Crowti is also distributed via exploit kits such as Nuclear, RIG, and RedKit V2,” Microsoft researchers say. This type of crimeware leverages vulnerabilities in Java (CVE-2012-0507) and Adobe Flash Player (CVE-2014-0515 and CVE-2014-0556).
Crowti has also been seen to be seeped in by other malware, such as Upatre dropper, Zemot or Zbot.
85,000 attacks recorded in 20 days
The latest version of CryptoWall is known to integrate a TOR (The Onion Router) component, designed to facilitate payment of the ransom. To lose the money trail, the fee has to be paid in digital currency and instructions on how to get it are offered in the ransom message.
CryptoWall is at the moment the biggest ransomware threat, exceeding CryptoLocker in the amount of money extorted from victims, as well as the overall number of infections worldwide.
In a report from Palo Alto Networks this month, it is stated that in less than 20 days during the month of October, no less than 84 variants of the malware were seen rampaging in the wild, being responsible for more than 85,000 attacks.
As Microsoft also observed, the operators behind this threat also used fraudulent digital certificates for code signing, in order to avoid detection. In one case, the certificate was issued for an entity called Trend (unrelated to security vendor Trend Micro).
Microsoft aligns to the general recommendation of not paying the ransom, on the grounds that there is no guarantee that the bad actors will keep their end of the deal and deliver the file unlocking key.
 14 DAY TRIAL //
14 DAY TRIAL //