The popularity of some videos with a pro-Russian view has grown lately on Dailymotion, as unknown actors increased their count artificially by using a piece of malware usually seen in financially motivated click-fraud campaigns.
Turning computers into bots that generate traffic to specific online locations showing advertisements is not a new tactic for making money, but choosing political videos for this purpose is far from being common.
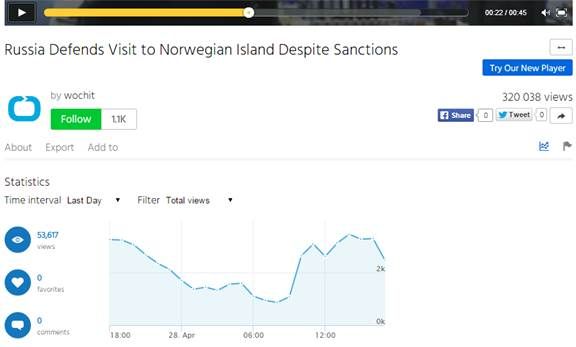
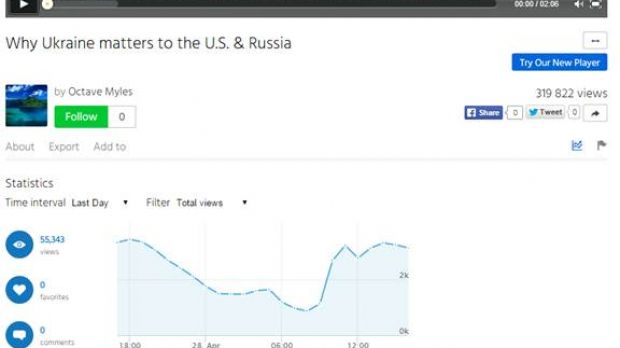
View count artificially increased to 320,000
Security researchers at Trustwave discovered that a website containing advice for tourists had been compromised by cybercriminals, who planted a malicious iframe that leads to Angler exploit kit (EK).
Systems with vulnerable browser plugins are then infected with Bedep, a Trojan known for ad-fraud operations. After installation, the malware loads the video locations without the victim being aware of the activity.
The visibility of a clip on the sharing website increases each time a bot accesses it, making it more valuable for advertisers.
However, it appears that, in this case, the malware also has a political agenda, and loads videos promoting views regarding Russia’s annexation of Crimea or other military and political matters.
Trustwave observed some patterns in these videos, such as a view count around 320,000, lack of shares, retweets or comments. Another thing in common is the availability of graphs that display the number of views with a filter set to “Last Day.”
Making money is still an objective
The researchers noticed that some of the videos Bedep pointed at were completely non-political, though, suggesting a monetary motivation of the campaign after all.
According to their analysis, the malware is instructed to create a hidden virtual desktop on the compromised computer, where a full-blown Internet Explorer is deployed. Furthermore, some of the pages loaded this way distributed two other exploit kits, Magnitude, and Neutrino.
“It seems that the guys behind this particular C&C are trying to maximize their profit by selling traffic from compromised computers to other campaigners that seek to spread their own malware via Magnitude and Neutrino. Just to make it clear: An already infected computer is visiting ads silently without the user's consent, and gets re-infected over and over again,” Rami Kogan from Trustwave writes in a blog post.
 14 DAY TRIAL //
14 DAY TRIAL //