Cybercriminals leverage the reputation and services of CareerBuilder employment website to distribute Word documents carrying exploits that deliver a backdoor with remote desktop connection capabilities.
Since the document comes from a reputable service, the victim has no reason to be suspicious and deploys the infection procedure. More than this, the document is more likely to circulate to multiple departments of a company, thus increasing the chances of infection.
Multiple infection points are available
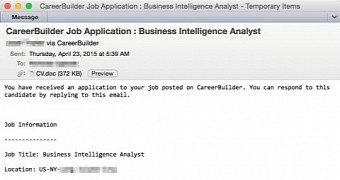
The crooks seem to leverage the fact that CareerBuilder does not process the documents received from the job candidates and passes them to the employers.
Security researchers at Proofpoint discovered the new malware delivery method and analyzed the steps leading to compromising the computers of an employer advertising a job opening on CareerBuilder.
“When a resume has been submitted to a listed job opening, the CareerBuilder service automatically generates a notification email to the job poster and attaches the document,” researchers write in a blog post.
They have noted that this approach requires more effort from the threat actor, but it is also more successful because the emails with the resumes are expected by the recipient.
Once a CV reaches an organization, it may be spread to employees in charge of recruiting new people: human resources, hiring manager, interviewer and/or stakeholders.
Backdoor uses TeamViewer to connect to infected host
Proofpoint says that the crooks do not have preferences when it comes to the type of the target and that the campaign is low-volume, with less than ten emails spotted. From their observations, among the intended victims are stores, companies in the energy sector, broadcasting, credit unions, electrical suppliers.
As far as the positions the threat actor applied for, these include “business analyst,” “web developer” and “middleware developer.” The requirements for these jobs permit tweaking the attack since they reveal the tools and software the organization is running.
The malware slung at the companies has been identified as Sheldor, a backdoor that includes the TeamViewer application for remote desktop connection. This way, the attack is more difficult to spot because TeamViewer is a legitimate solution that establishes the connection between the two machines by connecting them both to a reputable cloud service.
In order to drop it, Proofpoint says that the attackers create the malicious document using the Microsoft Word Intruder (MWI) exploit kit. Two of the vulnerabilities leveraged are CVE-2014-1761 and CVE-2012-0158.
Once a computer in an organization is compromised, the attacker can move laterally inside the network in search of more interesting targets.
 14 DAY TRIAL //
14 DAY TRIAL //