An email claiming to be from Australian telecommunications giant Telstra lures the recipient into opening an attached malicious file by informing them that it contains details about their business broadband cancellation order.
Even someone who does not have a business broadband plan with Telstra would probably be tempted to take a peek at the document, which is actually a PIF (Program Information File) file disguised as a PDF document.
PIF format – long time, no see
The cybercrooks used the classic double extension method to hide the true type of the file by giving it a name large enough to show only the first extension, PDF.
A true PIF does not contain executable code, but Windows runs them according to the content they store; as such, if there is something to execute, the operating system will run it.
This type of data has been historically associated with malware, but at the moment it is not used frequently; it may be that a comeback is in progress.
According to Hoax-Slayer, the full name of the malicious item is “PDF_copy_of_your_order_form.pdf.pif” but since the default configuration of Windows is to hide the extension, the PIF part is not seen in the built-in file manager, making the file appear as PDF.
Email may appear legitimate to the untrained eye
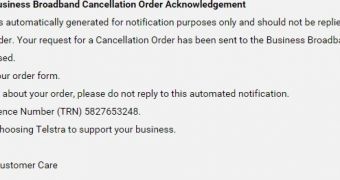
The fake email seems to be devised with care, as the crooks included details that contribute to making it appear legitimate communication from Telstra. They provide a reference number and inform the recipient that the message was sent automatically and therefore they should not reply.
“This email is automatically generated for notification purposes only and should not be replied to,” the message says, adding that the request for cancelling the subscription was sent to the Business Broadband Provisioning for processing.
“If you have a query about your order, please do not reply to this automated notification. Your Telstra Reference Number (TRN) 5827653248,” the message continues.
Basically, the recipient is given no real option to contact Telstra and only the illusion that this can be done has been created by including the reference number. Since it is easier to open the file in the attachment and verify the information it contains, many users will choose this option, thus compromising their computers.
To stay protected, it is recommended to avoid opening files from unknown sources, especially when their origin is an unsolicited message.
 14 DAY TRIAL //
14 DAY TRIAL //