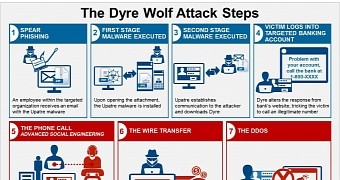
A cybercriminal group from Eastern Europe runs spear-phishing campaigns against organizations transacting large sums of money on a regular basis, delivering Dyre banking Trojan and stealing upwards of $1 million (€910,000).
Also known as Dyreza, the malware has been used from the beginning (June 2014) for stealing money from bank accounts.
DDoS used for confusion
In a recent campaign, the cybercriminals rely not only on the threat’s capability to harvest financial credentials but also on their social engineering skills, when attacking a company that relies on two approval codes to transfer large sums.
Dubbed “The Dyre Wolf” by security researchers at IBM, the operation is run by a resourceful group that also employs distributed denial-of-service (DDoS) attacks either to distract attention from the heist or to prevent the victim from logging into the bank account by the time they rob it.
Malware delivered by Upatre
Dyre reaches the victim’s computer through an email that carries Upatre downloader. The message baits the recipient to open the attached file purporting to be a document of financial importance, such as an invoice.
Once Upatre is installed on the system, it downloads and executes the malware, then it deletes itself. The researchers found that the entire process is dynamic, and the payload as well as the URLs it is funneled in from are constantly changing.
After achieving persistence and injecting the legitimate SVCHOST.EXE process, the malware establishes communication with a command and control (C&C) server hidden in the I2P anonymous network.
Dyre includes several web-injection tactics
The technique used by the threat to obtain the financial login data consists in serving fraudulent pages of the banks it targets, which is done via web injection.
One method to do it is to add extra text fields required for accessing the account, at the same time collecting the login username and password. Another way is to redirect the request for loading a targeted web page to Dyre’s server and send back a fake one that harvests any info entered.
A third method is to intercept the response from the bank and alter it so that new text fields are included before it reaches the victim.
Big money requires direct intervention
However, the most valued targets benefit from a different tactic that gets them in direct contact with the crooks over the phone. Instead of fake login pages, Dyre shows a site with an error message and a phone number, allegedly from the bank.
When the victim calls, a professional-sounding person with an American accent answers, replying that he works for the respective bank.
“After a brief conversation, this individual prompts the victim to give the username and password in question for the account and verifies it, several times. The attacker may also ask for a token code,” the report from IBM informs.
“Within this verifying stage, the attacker might ask to speak with a co-worker with similar access to the account, and who may be one of the authorized persons on that account, and ask them to verify information as well, and give a token code over the phone,” researchers add.
Cash bounces through multiple bank accounts
With both approval codes in hand, the attacker can then access the bank account and move the money and may initiate a DDoS assault (this happened in the case of one organization).
The cash is transferred through multiple accounts at foreign banks in order to avoid being detected by the financial institutions and law enforcement.
Losses between $500,000 (€450,000) and more than $1 million (€910,000) have been recorded in several reports. Sums this large are not easy to steal as these transfers trip alerts at banks; however, by focusing on companies that pass amounts this big on a daily basis, the cybercriminals ensure that alarms are not triggered.
 14 DAY TRIAL //
14 DAY TRIAL //