A fraudulent app for Android that allows users to top up contactless electronic tickets for public transportation, has been released last week in Chile.
Public transportation tickets in Chile, like in many other parts of the world, have evolved and near field communication is used to execute payment transactions.
Hackers in the country found a way to re-charge the cards (Tarjeta BIP) without actually shelling out the money, and created an app to facilitate the procedure. Basically, the code in the app allows modification of the information on the transportation card through direct interaction with the NFC port (android.hardware.nfc).
It goes without saying that a large amount of users hurried up and downloaded it, especially since they could also change the number of the card.
The government in Chile has successfully blocked about 10,000 such cards so far, but the effort should prove futile because the identification number of the card can be modified, the result being a fresh new card.
Potential for attacks targeting mobile phones
This type of abuse is not new, and has been demonstrated before at security conferences around the world, but in this case there is the potential of cybercriminals taking advantage of the popular app and deliver it to unsuspecting users with malware, said Dmitry Bestuzhev cyber threats researcher at Kaspersky.
An attack scenario is easy to imagine, since all bad actors have to do is host a fake copy of the app and promote it as the legitimate one.
The number of malicious activity they can carry out spans from spying on the victim’s communication to exfiltrating sensitive information used for online banking.
Because the app is hunted down by law enforcement, there is a better chance for users to lower their defenses and accept downloads from dodgy locations on the web promising a free ride.
App is now flagged by Kaspersky
Monetization attempts have already been recorded, Bestuzhev says, as a new version of the app appeared shortly after the initial launch, laced with advertisements from DoubleClik network a Google subsidiary for online ad services.
Kaspersky security solutions for mobiles running Android have included a signature to identify the fraudulent app, and it is now detected as HEUR:HackTool.AndroidOS.Stip.a.
Security researchers Corey Benninger and Max Sobell at Intrepidus Group demonstrated how transportation cards using NFC contactless technology could be reset for free travel. They held a presentation on the subject at the EuSecWest conference in 2012.
UltraReset - Using a smartphone for free subway rides from Intrepidus Benn on Vimeo.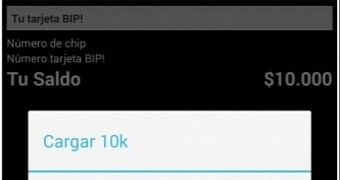
 14 DAY TRIAL //
14 DAY TRIAL //