Protesters in Hong Kong are targeted with an advanced spying tool for Android devices, which masquerades as an app for coordinating the pro-democracy movement dubbed Occupy Central.
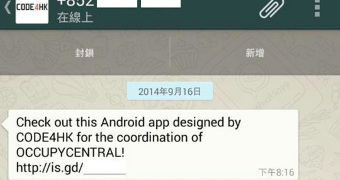
The malicious app is delivered through an anonymous WhatsApp message with a download link in it. The message says “Check out this Android app designed by Code4HK, group of activist coders, for the coordination of Occupy Central!”
Whoever sent the text preys on the notoriety of the Code4HK group of activist coders that want to improve government transparency in Hong Kong. The app is not developed by them, nor is the message sent by them.
Spyware capabilities are extensive
According to Lacoon Mobile Security, the Android spyware installs with an extensive list of permission for the app. In their hurry to access the software, many users do not properly scan what access they grant to an app.
At the first launch, the malware asks to be updated, which in fact activates the spying capabilities.
The type of information that can be exfiltrated with this tool ranges from the list of contacts, text messages, and call logs to multimedia files, emails, browser history, device identification information (phone number, IP address, SIM code) and geo-location based on the cell ID.
Lacoon notes that the Android malware can also make the compromised device accept files from a URL or a remote device or call a specific number. Researchers say that it allows the attacker to “execute commands within the “/system/bin/sh” directory as well as run “su” shell and a listen socket for commands before relaying results back to the CnC [command and control] server.”
Possible operators behind the spying tool
The mobile security company analyzed the data from the command and control (C&C) server and correlating it with the intended targets, believes that the Chinese government is running the attack. This would not be too far-fetched.
Based on their analysis, Lacoon determined that this is no ordinary spying tool, but an advanced one that is generally seen to be developed with government support.
On the same server the Android malware is downloaded from, the researchers found another spyware designed for iOS devices. It has roughly the same capabilities as its Android counterpart.
Lacoon dubbed it Xsser mRAT (mobile remote access Trojan) and labeled it “most advanced, fully operational Chinese iOS trojan found to date.” There is no information on how it is leveraged in attacks, though.
 14 DAY TRIAL //
14 DAY TRIAL //