Attackers with a server certificate can cripple the security of 25,000 iOS apps via man-in-the-middle (MitM) attacks and access in plain text the encrypted information sent from the client device.
The vulnerability is present in AFNetworking, a popular networking library for iOS and OS X products, and consists in failure to check the domain name the SSL certificate was issued for.
Any SSL certificate can be used to decrypt data
The feature exists in the product, but it is turned off by default in all AFNetworking versions prior to 2.5.3, which has been released on Friday.
“This meant that a coffee shop attacker could still eavesdrop on private data or grab control of any SSL session between the app and the Internet. Because the domain name wasn't checked, all they needed was a valid SSL certificate for any web server, something you can buy for $50 [€45],” reports SourceDNA, a company providing code analysis services.
Credited for the discovery of the flaw is Ivan Leichtling from Yelp. Ironically, AFNetworking maintainers had fixed the problem before the previous release (2.5.2), which emerged to repair another SSL-related vulnerability, but somehow it was not included.
The issue eliminated in AFNetworking 2.5.2 was a lack of SSL certificate validation, allowing an attacker with a self-signed certificate and in a position to intercept encrypted traffic from vulnerable apps to view the sensitive info sent to the server.
After scanning for vulnerable code present in iOS apps, SourceDNA found that after the flaw was patched there were plenty of developers that had not updated their products, leaving their users exposed.
Big name devs have vulnerable apps
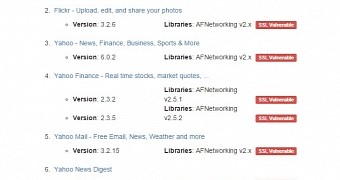
Based on its scan results for iOS products with the domain name validation turned off, on Friday there were more than 25,000 iOS apps affected by the flaw, the company says.
Apps from important developers, such as Yahoo and Microsoft, that had patched against the SSL certificate validation flaw are now again vulnerable.
SourceDNA makes available a free online service that allows developers and users check if their apps are susceptible to attacks.
Developers are advised to integrate the new AFNetworking build into their products in order to have domain name validation enabled by default.
 14 DAY TRIAL //
14 DAY TRIAL //