The latest firmware version for Business Storage 2-Bay NAS devices from Seagate relies on vulnerable versions of PHP and CodeIgniter for the web-based administration console, allowing a remote attacker to execute arbitrary code.
A threat actor does not have to be authenticated to exploit the glitches and they would be able to run code under the context of the root user, allowing complete control of the device and potentially gaining access to other devices in the network.
PHP, CodeIgniter flaws open multiple attack avenues
Security consultancy company Beyond Binary discovered that the management application included with firmware 2014.00319 is built with PHP 5.2.13 (builds 5.6.6, 5.5.22 and 5.4.38 are available) and CodeIgniter 2.1.0 (build 2.2.1 is currently available), which have known security flaws.
In the case of PHP, an old security flaw (CVE-2006-7243) allows null byte injection (“\0”), which truncates anything beyond it; this would allow an attacker to bypass access restrictions by placing a safe file extension after the null byte and upload malicious code through require() and include() functions.
In the case of the glitchy version of CodeIgniter, an open source web application framework included in Seagate’s NAS devices, the encryption key used to create the session token can be extracted and used to decrypt the session cookie.
Altering the content of the cookie could result in additional avenues of attack, such as PHP object injection, the researchers say.
The trouble runs deeper than this, though, as Beyond Binary reports that Seagate uses the same encryption key on its entire line of affected NAS devices.
Custom web app has issues of its own
Another issue found by the security researchers touches on the custom web application included by Seagate in its Business Storage 2-Bay NAS products.
“The custom web application does not appear to maintain session-related information on the web server side. All of the information relevant to a user session is stored inside the session cookie prior to it being encrypted and sent to the browser,” Beyond Binary explains.
According to the researchers, the cookie includes the username value as well as a string indicating if the user is an administrator or not. They say that the cookie does no validate user credentials if the “username” is available, allowing complete bypass of the log-in procedure.
Since the same static encryption key is used for all instances of the console, it means that one valid session cookie works on all of them, Beyond Binary concludes.
The web app is served by open-source web server Lighttpd, which runs with the highest privileges (root).
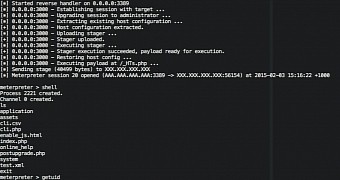
Metasploit module created, firmware update not released
The researchers tested their findings on the latest firmware version (2014.00319) for the products as well as build 2013.60311.
As far as the number of products potentially impacted by the findings are concerned, the security experts say that, using Shodan search engine for Internet-connected devices, they received more than 2,500 results.
On October 22, 2014, Beyond Binary delivered Seagate a report explaining the security risks in firmware version 2014.00319, and on January 25, 2015, the hard disk manufacturer confirmed the validity of the proof-of-concept (PoC).
Initially, Beyond Binary set a public disclosure period of 100 days for these issues, which expired on January 30, 2015, but the company provided an extension until March 1.
The latest response on the matter from Seagate came on February 26, informing that there was no update to be shared. As such, on Sunday, Beyond Binary made its findings public.
The company developed and published a Metasploit module and a Python script that automate exploitation of the flaws.
 14 DAY TRIAL //
14 DAY TRIAL //