A fresh strain of Zeus banking Trojan has been discovered in the wild, with a configuration file that targets more than 150 banks and 20 payment systems mostly in countries in Europe.
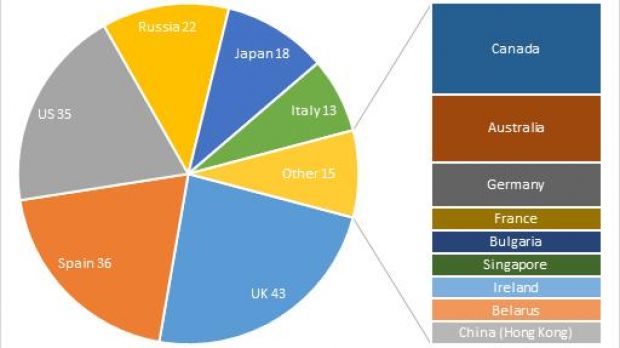
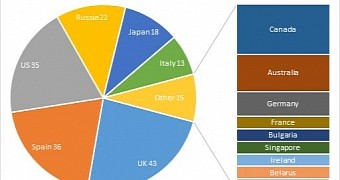
The malware, dubbed Chthonic, relies on a new method for loading its modules and is prevalent in the UK and Spain. Infections have also been observed in other European countries, although in lower numbers, on machines in Italy, Germany, France, Bulgaria, and Ireland.
On the list of most affected countries, the US takes the third place, according to data from Kaspersky, followed by Russia and Japan.
It is distributed to the victims through the Andromeda bot, as well as through an exploit for a vulnerability (CVE-2014-1761) in Microsoft Office, which comes via email.
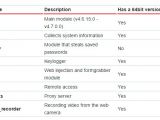
Most malware modules are compatible with 64-bit systems
Researchers say that the new banking Trojan combines the encryption scheme from other strains of Zeus, as well as a virtual machine seen in ZeusVM and KINS malware. Moreover, it has been observed that the same encryptor as the one in Andromeda threat is responsible for creating the botnet with the same name.
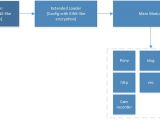
It seems that Chthonic features a new method for loading malicious modules, researchers say. This is achieved through a main module that proceeds to download all the other components of the malware, then it starts loading them. The AES specification is used for encryption.
During the analysis of the malware, the security experts from Kaspersky noticed that most of the malware components were compatible with both 32-bit and 64-bit platforms.
Among the capabilities of Chthonic there is collecting system information, stealing passwords from the system through Pony malware, recording computer activity (keylogger), web injection, form grabbing, and remote access to the compromised machine through VNC remote desktop software.
Not all attack attempts are successful
Relying on the man-in-the-middle technique, the Trojan intercepts communication from the client to the targeted bank and modifies the web page loaded in the browser so that sensitive banking information (log-in details, PIN, one-time password) is obtained from the victim.
If warnings of fraud attempt are issued by the bank on the loaded page, these are automatically hidden.
Kaspersky says that, in the case of Russian customers, the bank’s page is spoofed in its entirety instead of just parts of it, a method not seen in regular attacks of this kind.
It appears that despite the large number of targets included in the configuration file, the list has not been curated, and in many cases. an attack would not work.
“It is worth noting that, in spite of the large number of targets on the list, many code fragments used by the Trojan to perform web injections can no longer be used, because banks have changed the structure of their pages and, in some cases, the domains as well,” it is explained in a report from Kaspersky.
Chthonic is the result of the Zeus code having been leaked on underground forums. This allowed different actors to come up with their version of the malware.
 14 DAY TRIAL //
14 DAY TRIAL //