Security researchers identified a fresh malware piece targeting point-of-sale (PoS) systems that relies on encrypted communication to exfiltrate payment card info from the memory of the payment processing machines.
By sending data using SSL (Secure Sockets Layer), hackers ensure that detection at network level is more difficult since the details of the communication cannot be analyzed.
Malware download server hosts threats for different purposes
The threat, dubbed NitlovePoS by security researchers at FireEye, is delivered discriminately, from a server hosting a herd of malware, after cybercriminals first identify the nature of the victim.
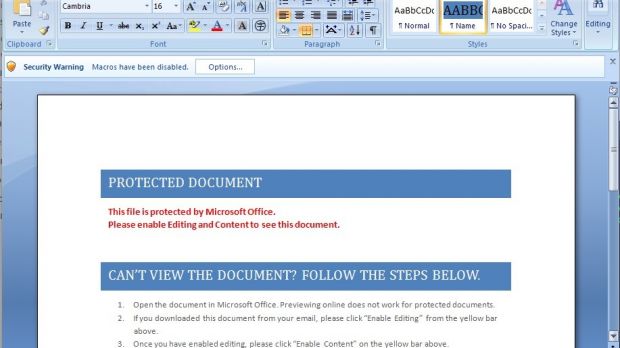
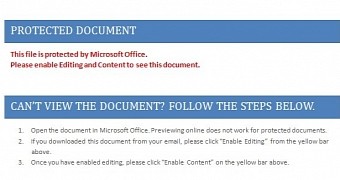
The infection starts with a spam email that purports to come from someone looking for a job, who delivers a Word document rigged with a malicious macro script, whose support is disabled by default in Microsoft Office components.
To trick the recipient into enabling the functionality, the document claims to be protected and offers instruction on how its content can be revealed. Once the macro script feature becomes active, a malware downloader is automatically funneled in and installed.
FireEye says that the initial payload has multiple updates, in an effort to avoid detection. The server it contacts for getting the main malware piece hosts several threats (more than 10 pieces), each probably being intended for different types of victims.
Analysis efforts, however, were focused on NitlovePoS (present on the server under the name pos.exe), which was downloaded three times, a low number compared to other pieces available.
Command and control server located in Russia
NitlovePoS seems to be actively maintained as a new version was uploaded on Friday, although it does not include additional functionality, just a different file structure.
Researchers found three threats available in the PoS malware, one for secure communication with the command and control (C&C) server (located in St. Petersburg, Russia), one for storing the card data in memory and one for scraping the card data from other processes loaded in the computer memory.
“When executed, [NitlovePoS] will copy itself to disk using a well-known hiding technique via NTFS Alternate Data Streams (ADS),” a blog post from FireEye explains, adding that a VBS script is then created and stored on the disk, also using ADS.
Both files are saved in a location on Windows that is not easily accessible by the user. Selecting this method ensures that the files are more difficult to locate because they are not visible in the file system. Furthermore, the items are given the name “defrag,” designed to make them pass as legitimate files required by the system.
NitlovePoS searches for Track 1 and 2 data
To achieve persistence, the malware adds itself to the Run registry key, allowing it to restart at every computer reboot. The VBS script also monitors the malicious process and redeploys it if deleted.
Once everything is set up, NitlovePoS starts searching for track 1 and track 2 information gathered from the magnetic stripes of the cards swiped through the PoS terminal.
The two data tracks contain all the information necessary for cloning cards or for making fraudulent online purchases.
 14 DAY TRIAL //
14 DAY TRIAL //