Another zero-day vulnerability has been discovered in Adobe Flash Player and it is currently exploited by cybercriminals via a malvertising campaign on Dailymotion video sharing website.
The flaw, which has been assigned the identifier CVE-2015-0313, is present in Flash Player 16.0.0.296 and the exploit is delivered to computers running all versions of Internet Explorer and Mozilla Firefox, on Windows 8.1 and earlier, Adobe says in a security advisory posted on Monday.
Malicious advertisements published on Dailymotion
Initial analysis from security researchers suggests that the code taking advantage of the flaw is delivered by Angler exploit kit, a malicious tool that has been used with two other zero-days that prompted Adobe to release out-of-band security updates for Flash.
Threat analyst Peter Pi from Trend Micro says that the results of the investigation show that Dailymotion visitors are redirected to multiple online locations, in the end landing on a page hosting the exploit (retilio[.]com/skillt[.]swf).
Pi is credited for reporting the flaw to Adobe, along with Elia Florio and Dave Weston of Microsoft.
“It is important to note that infection happens automatically, since advertisements are designed to load once a user visits a site. It is likely that this was not limited to the Dailymotion website alone, since the infection was triggered from the advertising platform and not the website content itself,” a blog post from Pi informs.
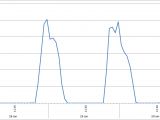
Hits on malicious URL spike on January 27
Trend Micro has been keeping an eye on the attack since January 14, and a week later, on January 27, they noticed increased activity related to the malicious IP.
This would be the day when Adobe published the security advisory announcing that Flash Player 16.0.0.296 closed a then second zero-day (CVE-2015-0311) and became available for all supported platforms; CVE-2015-0311 had been exploited in the wild with Angler for a week, since January 20.
As per telemetry data from Trend Micro, most of the systems compromised in this attack are from the United States. They observed 3,294 hits related to the exploit. At the moment, the malicious advertisements connected to the infection chain observed by Trend Micro appear to be down.
However, researchers warn that other attacks may be leveraging the zero-day vulnerability in Flash Player and recommend that the browser plug-in be disabled until Adobe issues a safe version. Given the critical severity of the issue, an update is expected to appear this week.
[UPDATE, February 3]: Security researcher Kafeine determined that the exploit kit used for the attacks is not Angler but another tool called Hanjuan Exploit Kit.

 14 DAY TRIAL //
14 DAY TRIAL //