Reports about fileless malware that leaves no trace on the disk and resides in the memory of the system have been sporadic, but things are likely to change, as a new strain of this type of threat has been spotted on sale on underground forums.
Dubbed Phasebot, the malware is believed to have spawned from Solarbot, known since at least May 2013, due to functional similarities. However, the new version focuses on evading detection, Michael Marcos, threat response engineer at Trend Micro, has discovered.
Malware can steal login info, encrypts connection with C&C
The main feature of Phasebot consists in keeping itself hidden from antivirus solutions by lodging in the memory of the compromised computer, thus remaining unaffected by security products sweeping the hard disk.
It can also detect virtual machines, which are used by researchers to analyze malware behavior in a safe environment, and relies on encrypted communication with the command and control (C&C) server. Marcos says that Phasebot uses a different password each time it contacts the control center.
According to the researcher, the malware includes an external module loader, which is used for adding or removing malicious components on the compromised machine.
Among the capabilities of the threat there is stealing information from websites by using form-grabbers, running distributed denial-of-service (DDoS) attacks, updating itself, as well as downloading and executing other files (modules for remote desktop control) and stealing card data from point-of-sale systems.
Malicious shellcode is hidden in Windows Registry
Phasebot’s post-infection behavior is similar to Poweliks’, another fileless threat spotted several times since late July 2014.
In fact, Phasebot itself was documented in December 2014 in a very detailed write-up from MalwareTech, which said it had gone on sale in late October 2014, for $200 / €185.
During the initial steps, the system is checked for the presence of .NET Framework 3.5 and Windows PowerShell, which help run the malicious components.
Since it resides in the memory and a system restart would remove it, the malware achieves persistence by placing encrypted shellcode for both 32-bit and 64-bit platforms in Windows Registry, with the values “Rc4Encoded32” and “Rc4Encoded64.”
Then, another registry entry is created with the name JavaScript, whose purpose is to decrypt and execute the shellcode via PowerShell.
If PowerShell and .NET Framework are not present on the infected system, Phasebot switches to rootkit tactics and hooks “NtQueryDirectoryFile” API and “NtReadVirtualMemory” to hide the file and the malware process.
“We expect that more malware writers will soon be adopting and adapting the fileless concept. It’s highly possible that they will not limit themselves to simply using the Windows registry to hide their malware. They will also use other, sophisticated techniques to run malicious routines without having to drop a file into the affected system,” Trend Micro researchers say.
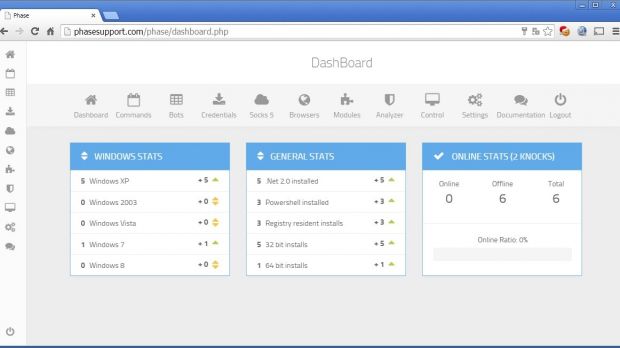
In January 2015, malware researcher Xylit0l published a large list of images with Phasebot's administration console.
 14 DAY TRIAL //
14 DAY TRIAL //